Tips and Best Practices for API Authentication
With APIs being used for everything, almost every system we build or service we use depends on APIs. While APIs enable integration between systems and drive innovation, they expose sensitive data and functionalities to potential unauthorized access and security threats.
API authentication serves as the primary mechanism for verifying the identity of entities attempting to interact with an API. Developers can ensure that only legitimate users and applications have access by establishing an authentication process for their APIs. When it comes to securing APIs, secure authentication protocols, such as OAuth and OpenID, provide an additional layer of security for authenticating different users, applications, and API clients. In this blog, we will explore the technical aspects of API authentication, covering various methods and implementation best practices that can be used by API providers. Let's begin by looking closer at the fundamentals of API authentication.
Introduction to API Authentication#
Whether a mobile app fetches data from a server, a web application integrates with third-party services, or microservices communicate within a distributed system, APIs are the backbone of most digital experiences nowadays.
However, the open nature of APIs also exposes them to many potential security risks. Without the proper security measures, malicious actors can easily exploit vulnerabilities, gain unauthorized access to sensitive data, disrupt services, or manipulate information. This is where API authentication is a critical component in API security. For developers, understanding and implementing API authentication is one of the most essential skills to have in their toolkit for building APIs.
Definition and Importance of API Authentication#
API authentication is a critical process that verifies a client's identity when accessing an API. This verification ensures the client is who they claim to be, preventing unauthorized entities from accessing sensitive data or functionalities exposed through the API. Without proper authentication, APIs are vulnerable to various attacks, including:
-
Data breaches: Unauthorized access can lead to the exposure or theft of confidential information.
-
Service disruption: Malicious actors can exploit unsecured APIs to disrupt services or manipulate data.
-
Financial loss: Unauthorized API use can result in economic losses due to fraudulent transactions or resource misuse.
-
Reputation damage: Security breaches can damage an organization’s reputation and negatively impact customer trust.
API authentication is critical in mitigating these risks and ensuring the security and integrity of API-based systems.
API Authentication vs Authorization#
While often used interchangeably, API authentication and authorization are distinct yet interconnected concepts in API security. When developers talk about an API being "protected," this usually encompasses an API that has both authentication and authorization implemented. Here's a brief comparison of the two.
-
Authentication: Authentication verifies the client's identity. It answers the "Who are you?" question by validating the credentials provided (e.g., username and password, API keys, and tokens).
-
Authorization: Authorization determines what actions an authenticated client is permitted to perform. It answers the question, "What are you allowed to do?" Authorization typically involves assigning permissions or roles to clients and controlling their access to specific API resources and operations.
Simply put, authentication establishes the client's identity, while authorization defines and enforces their access rights within the API. These two processes work together to create the security framework for accessing APIs securely.

Over 10,000 developers trust Zuplo to secure, document, and monetize their APIs
Learn MoreAPI Authentication Methods#
When it comes to adding authentication to an API, developers have several authentication methods they can use to secure APIs. Each has its own strengths and weaknesses, leaving developers to decide the best one for their use case and the security level they require. Let's look at a few of the most popular API authentication methods.
Basic Authentication#
Basic authentication is the simplest form of API authentication. It involves sending a username and password with each request, encoded in Base64 format within the Authorization header. While easy to implement, basic authentication is inherently insecure, as credentials are transmitted in plain text and susceptible to interception. It's generally recommended to use basic authentication only over HTTPS to encrypt the transmission of plain-text passwords.
API Key Authentication#
API key authentication relies on a unique identifier (the API key) that clients include in their requests, typically in the headers or query parameters. The server validates the key against a list of authorized keys. Since API keys are relatively simple to manage, they are an extremely popular way to protect APIs. Unfortunately, they offer limited security if not adequately protected, so ensuring that developers and key management platforms handle keys securely is critical to security. They are suitable for scenarios where user-specific authentication isn't necessary since many users could technically use a single API key.
Token-Based Authentication#
Token-based authentication involves issuing a temporary token to the client application after successful authentication. This token is then included in subsequent requests, usually in the Authorization header as a Bearer token. Access tokens offer better security than API keys as they are temporary and can be revoked or rolled (replacing the old key with a new one) if compromised.
OAuth Authentication#
OAuth (Open Authorization) is a widely used authorization framework that enables secure access to protected resources on behalf of a user without sharing their credentials directly. It's commonly used for social logins and integrations with third-party services. OAuth provides various grant types to suit different use cases, such as authorization code grant for web applications and client credentials grant for machine-to-machine communication.
REST API Authentication#
While REST (Representational State Transfer) is an architectural style for designing networked applications, it doesn't inherently define an authentication method. REST APIs typically employ one or more authentication methods (Basic, API keys, tokens, OAuth) to secure access to their resources. The choice depends on factors like the sensitivity of the data, the types of clients accessing the API, and the desired level of security.
Advanced API Authentication Methods#
While the basic authentication methods provide a solid foundation for API security, we can build off of these for enhanced capabilities and security features. For example, secure authentication protocols like OpenID and Mutual TLS give an additional layer of protection for authenticating different users, applications, and API clients. Let's look at three additional technologies developers can use to secure APIs.
JWT Authentication (JSON Web Token)#
JWT (JSON Web Token) is a compact, self-contained way to securely transmit information as a JSON object between parties. It's often used for authorization but can also be used for authentication. JWTs consist of three parts:
-
Header: Contains information about the token type and the algorithm used for signing.
-
Payload: Contains the claims (data) about the authenticated user or entity.
-
Signature: A cryptographic signature that verifies the token's authenticity and integrity.
JWTs are stateless, meaning the server doesn't need to store session information. This makes them suitable for scalable and distributed systems. They can also be easily used with various programming languages and platforms, as many have middleware and SDKs that allow developers to leverage this approach. Like other methods, proper key management and token expiration are still crucial for security.
OpenID Connect (OIDC)#
OpenID Connect (OIDC) is an identity layer built on the OAuth 2.0 protocol. It extends OAuth by providing a standardized way for clients to verify the end user's identity and obtain basic profile information about them. OIDC is often used for single sign-on (SSO) scenarios, allowing users to authenticate with multiple applications using a single set of credentials. OIDC-protected APIs will still use JWTs, which we mentioned above, to authenticate and authorize the user.
Mutual TLS (mTLS) Authentication#
Mutual TLS (mTLS), known as certificate-based authentication, involves using digital certificates for the client and server to establish a secure connection. It provides a strong form of authentication, as certificates are difficult to forge. However, it can be more complex to implement and manage than other methods. mTLS is often used when high security is paramount, such as in financial transactions or communication between internal services. Zuplo offers an easy way to implement mTLS by allowing developers to add an mTLS inbound policy.
As mentioned, many APIs provide one or more of the authentication methods above for developers to authenticate and connect. Zuplo includes support for these authentication mechanisms out of the box, so developers can get up and running in minutes.
Best Practices for Secure API Authentication#
Even with your authentication in place, it needs to follow some steadfast rules for it to be effective. When it comes to REST API authentication methods, let's look at a few best practices to implement and follow.
Enforce Strong Passwords and Implement Password Hashing#
When passwords are used (e.g., in Basic authentication), enforce strong password policies requiring a combination of uppercase and lowercase letters, numbers, and special characters. It's also important to never store passwords in plain text. Instead, employ hashing algorithms (e.g., bcrypt, Argon2) to store password hashes securely.
Implement Token Revocation for Token-Based Authentication#
If you use token-based authentication, ensure you have a mechanism for access token revocation. This allows you to invalidate tokens if they are compromised or when a user logs out. You can implement revocation using blacklists, rotating keys, or short token lifespans to ensure that tokens remain secure.
Limit Session Length#
For session-based or token-based authentication, set appropriate session or token expiration times. Shorter lifespans reduce the window of opportunity for unauthorized access if a session or token is stolen. You can also consider implementing refresh token mechanisms to balance security with user experience.
Implement Access Control Lists (ACLs)#
ACLs define fine-grained permissions for authenticated users or clients. Using an ACL, you can control which resources or actions they can access by associating specific permissions with each user or API client. Use ACLs to implement the principle of least privilege, granting only the minimum necessary access that the user needs.
With these best practices, you can ensure that your approach to API authentication starts on the right foot. Next, we will go further into factors to consider when choosing which type of authentication is the best fit for your APIs.
Evaluating API Authentication Methods#
Choosing a suitable authentication method is a critical decision that impacts your API's security, usability, and scalability. There are two areas you'll want to focus on when looking at which to use. First, you want to look at the functional factors of the API authentication method you're considering, such as its usability and scalability. Then, you'll want to take a closer look to ensure it checks off all of the security boxes you require, such as authentication strength and how vulnerable the authentication mechanism is to malicious attacks. Let's look closer.
Considerations for Choosing an Authentication Method#
When evaluating API authentication methods, consider the following factors:
-
Security Requirements: Assess the sensitivity of the data your API handles. For highly sensitive data, more robust methods like OAuth, OIDC, or mTLS might be necessary.
-
Client Types: Consider the types of API clients that will be accessing your API (web applications, mobile apps, IoT devices, etc.). Choose a method that aligns with their capabilities.
-
Scalability: If your API needs to handle a large number of requests, opt for stateless authentication mechanisms like JWT or API Keys, which scale better than session-based authentication.
-
Usability: Strive for a balance between security and user experience. Complex authentication flows can deter developers and cause them frustration. Choose a method that is both secure and easy for your developers to understand and implement.
-
Regulatory Compliance: Be aware of industry-specific regulations or data privacy laws that may require the use of specific authentication methods within your APIs.
How to Evaluate the Security of an Authentication Method#
To assess the security of an authentication method, consider the following aspects:
-
Confidentiality: Does the method protect credentials from unauthorized disclosure during transmission? Look for methods that use encryption (HTTPS) and avoid transmitting credentials in plain text.
-
Integrity: Does the method ensure that messages and data are not tampered with during transmission? Methods like JWT and Hawk use cryptographic signatures to protect against data modification.
-
Authentication Strength: How resistant is the method to brute-force or replay attacks? Consider methods that use strong passwords, token expiration, and rate limiting to enhance security.
-
Token Management: For token-based methods, evaluate how tokens are generated, stored, and revoked. Proper token management is crucial for preventing unauthorized access.
-
Vulnerability to Attacks: Research known vulnerabilities and attacks associated with the authentication method you're considering. Choose methods with a good security track record and stay updated on emerging threats.
Adding API Authentication With Zuplo#
Zuplo significantly helps streamline the implementation of various API authentication methods for your APIs. It provides a user-friendly interface and pre-built policies that make it easy to secure your API endpoints without writing extensive custom code.
For example, for API Key authentication, Zuplo allows you to easily generate and manage API keys. You can associate these keys with individual consumers, giving you fine-grained control over who can access your API. Applying the API Key policy to specific routes ensures that only requests containing valid API keys can access said routes.
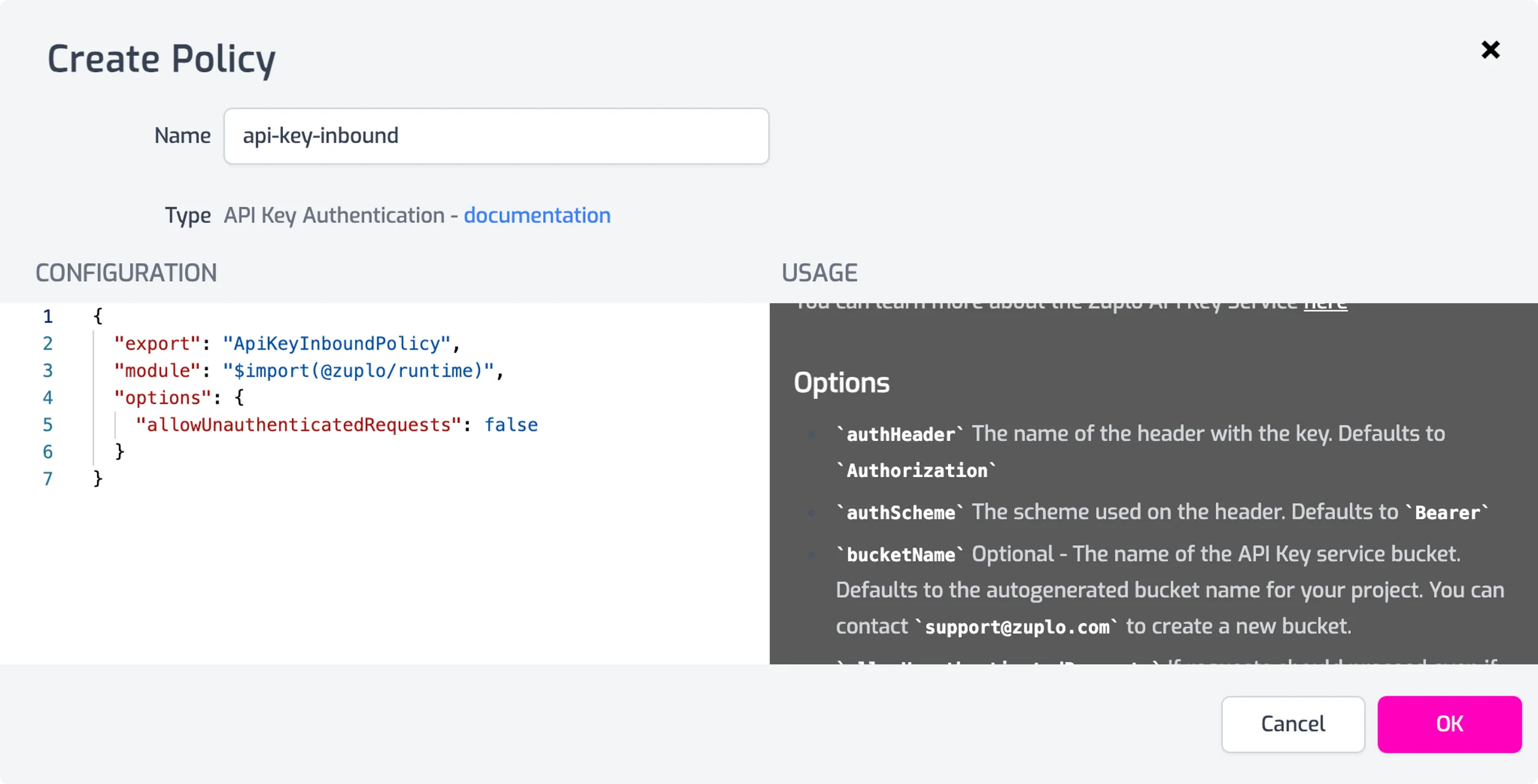
Similarly, Zuplo provides a "JWT Auth" policy for JWT authentication. You configure the expected issuer and audience of the JWTs, and Zuplo verifies the token's signature, expiration, and any additional claims you define before giving access to the API.
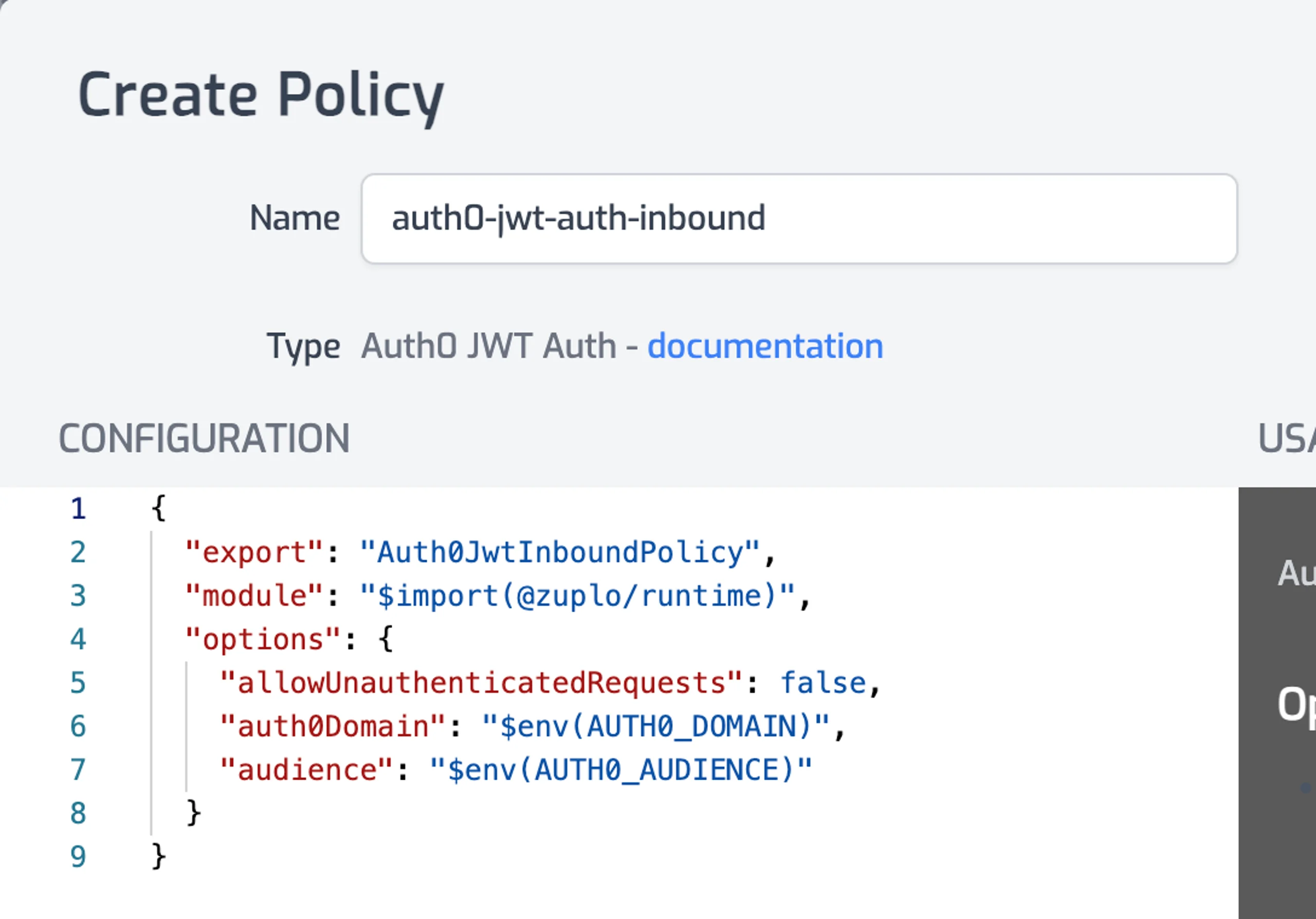
By leveraging Zuplo's capabilities, you can quickly add authentication mechanisms to your APIs with minimal effort, focusing more on developing your core API functionality and less on the intricacies of implementing API authentication and authorization.
Conclusion#
API authentication is a cornerstone of modern API security. Choosing and implementing the right authentication method can safeguard your data, protect your users, and build trust in your API ecosystem. Understanding the various techniques available, from basic authentication to advanced methods like JWTs, OIDC, and mTLS, empowers you to make informed decisions based on your specific needs and security requirements.
If you want a streamlined way to implement and manage API authentication, Look no further than Zuplo. With a developer-first approach to API management and powerful features, Zuplo is an excellent choice for making it easy to add robust security to your APIs without sacrificing development time or flexibility.
Sign up for a Zuplo account today and discover how easy it is to secure your APIs with our developer-first API management platform.








