Simple HTTP Authentication: A Beginner’s Guide
As API security evolves, striking the right balance between protection and simplicity is crucial. While modern authentication methods like OAuth and JWT have gained popularity for their robust features, there’s still a place for the tried-and-true HTTP Basic Authentication. You’ve likely encountered it countless times when a browser or app pops up a simple username/password dialog. It is essential to use a secure connection (HTTPS/TLS) when employing HTTP Basic Authentication to ensure credentials are transmitted in an encrypted manner. While other authentication methods have emerged, Basic Authentication remains a relevant and practical solution, particularly when a simple, lightweight approach to API security is desired. This overview will cover the mechanics of HTTP Basic Authentication, its continued applicability, and best practices for secure implementation, particularly within the context of the Zuplo API gateway.
What is HTTP Basic Authentication?#
HTTP Basic Authentication is a straightforward protocol that allows a client to provide a username and password when requesting access to a protected resource. This method, known as the 'Basic' HTTP authentication scheme, transmits user ID/password pairs encoded using Base64, a simple encoding scheme that converts the username and password into a string of characters. When working with APIs, Basic Authentication is a common access control method. If the requested resource requires authentication, it will respond with a 401 Unauthorized status to any request lacking valid credentials. In such a scenario, the client can resend the request, incorporating the Authorization header, which includes the Base64-encoded username and password. This Basic authentication scheme transmits credentials as user ID/password pairs, encoded using Base64 for a basic level of security.
Basic Authentication vs Modern Authentication#
While Basic Authentication can be quick and easy to implement, it has some limitations compared to more modern authentication methods:
- Security: The basic authentication scheme encodes credentials in Base64, which is not encrypted, making them vulnerable to interception without additional security measures like HTTPS/TLS.
- Token Management: It doesn’t have a built-in mechanism for managing tokens or sessions, making it less flexible for scenarios where you want to revoke access or implement expiration times.
- Two-Factor Authentication (2FA): Basic Authentication doesn’t natively support 2FA, an important security layer for protecting accounts. Modern authentication methods like OAuth 2.0 and JSON Web Tokens (JWT) address these limitations. OAuth provides a more comprehensive protocol that allows delegated authorization and supports 2FA. JWTs are self-contained tokens capable of carrying additional data and offering built-in expiration mechanisms, enhancing security and flexibility.
Why Use Basic Authentication?#
Despite its limitations, Basic Authentication retains its relevance in certain scenarios. It shines in situations where simplicity is critical, such as with internal applications or APIs where security requirements are less stringent. Its ease of understanding, implementation, and debugging makes it an attractive option for developers seeking a quick and straightforward authentication solution. Basic Authentication can restrict access to specific sections of a website or API, adding a layer of protection without introducing unnecessary complexity. It remains a viable choice for legacy systems that may not support newer authentication mechanisms, ensuring continued functionality and security for these older platforms. During prototyping or initial API testing phases, Basic Authentication can be deployed quickly to establish a preliminary layer of protection, allowing developers to focus on core functionality before implementing more robust authentication measures later in the development lifecycle.

Over 10,000 developers trust Zuplo to secure, document, and monetize their APIs
Learn MoreHow HTTP Basic Authentication Works#
The process of HTTP Basic Authentication follows a simple challenge-response flow:
- Request: The client sends an initial request to access a protected resource on the server.
- Challenge: If the resource requires authentication, the server responds with an HTTP status code 401 Unauthorized. This response includes a WWW-Authenticate header field that specifies the authentication scheme (Basic) and an optional realm, which is a descriptive text about the protected area.
- Credentials: The client receives the challenge and prompts the user for their username and password (often via a browser dialog). The client provides authentication information (username and password) to the server in the HTTP authentication framework.
- Encoded Credentials: The client combines the username and password in the format “username” and encodes this string using Base64.
- Authorization Header: The client sends a new request, including an Authorization header. The value of this header is “Basic” followed by a space and then the Base64-encoded credentials.
- Verification: The server receives the request, decodes the credentials from the Authorization header, and validates them against its user database or authentication provider.
- Success or Failure: If the credentials are valid, the server grants access to the resource and returns the requested data. If not, it returns another 401 Unauthorized response. This challenge-response mechanism, while simple, forms the backbone of basic access control for numerous web resources.
The Role of the Authorization Header#
The Authorization header is a standard HTTP header that's essential to Basic Authentication. It's used to transmit user credentials to the server. An example of an authorization header would be Authorization: Basic dXNlcm5hbWU6cGFzc3dvcmQ=. The header's value is made up of the following:
- Authentication Scheme: This is always “Basic” for Basic Authentication.
- Credentials: The Base64-encoded string containing the username and password concatenated with a colon.
In this example, dXNlcm5hbWU6cGFzc3dvcmQ= is the Base64 encoding of username:password. While Base64 provides a simple encoding mechanism, it's important to remember that it doesn't offer encryption. Therefore, using HTTPS alongside Basic Authentication is crucial to ensure secure transmission of credentials.
User Agent and HTTP Basic Authentication#
A user agent, typically a web browser, plays a crucial role in Basic Authentication. When a user agent encounters a 401 Unauthorized response with the WWW-Authenticate header indicating Basic Authentication, it will usually:
-
Prompt the User: Display a dialog box asking the user to enter their username and password.
-
Handle Credentials: Collect the credentials, encode them as described above, and include the Authorization header in the next request.
-
Caching: Most browsers will cache valid credentials for a certain period to avoid repeatedly asking the user for their login information. User agents may also handle proxy authentication by providing credentials to a proxy server.
Implementing HTTP Basic Authentication#
Implementing Basic Authentication involves configuring your server to challenge unauthenticated requests and validating the credentials provided in the Authorization header. Let’s explore how this works in different server environments and outline some best practices for security. To configure proxy authentication, you must handle the 407 (Proxy Authentication Required) status code. This involves using the Proxy-Authenticate header to specify the authentication method that the client must use to access the resource. The client then responds with the Proxy-Authorization header, providing the necessary credentials for the proxy server. Proper handling of proxy authentication ensures secure access to resources through a proxy server.
Configuring Servers for Basic Authentication#
How Basic Authentication is implemented varies depending on your server technology; however, the core concepts remain consistent across different platforms. Here's a brief overview of how it's implemented in some common scenarios:
- Apache HTTP Server: Use the mod_authn_core and mod_auth_basic modules. You’ll define a .htpasswd file to store usernames and their hashed passwords and then configure directives in your .htaccess file (or virtual host configuration) to protect specific directories or resources.
- NGINX: Similar to Apache, you’ll utilize the auth_basic directive and a password file (often generated with the htpasswd utility). You’ll then specify which locations in your configuration should be protected. To handle the 407 (Proxy Authentication Required) status code, configure the Proxy-Authenticate and Proxy-Authorization headers to manage the challenge and response mechanism for proxy authentication.
- Node.js (Express): Use middleware like basic-auth to handle authentication. You’ll provide a function to validate credentials and configure which routes require protection.
- Zuplo (API Gateway): Zuplo simplifies Basic Authentication setup by allowing developers to enable it with a few clicks, providing the list of valid username/password combinations directly in the Zuplo dashboard. More specifics can be found a bit later in this blog! Regardless of the technology stack used, there are common best practices that will ensure the security of your Basic Authentication implementation.
Best Practices for Secure Implementation#
To mitigate the inherent risks associated with Basic Authentication and improve security, it's important to follow best practices during implementation. These measures help create a more secure environment for your applications and APIs:
- HTTPS: Always use HTTPS to encrypt the transmission of credentials. Basic Authentication over plain HTTP protocol is insecure because the encoded credentials can be easily intercepted. Using HTTPS/TLS is crucial to protect sensitive or valuable information when using Basic Authentication.
- Strong Passwords: Enforce strong password policies for your users, making it harder for attackers to guess credentials.
- Hashing: Never store passwords in plain text. Always use a secure hashing algorithm (like bcrypt or Argon2) to store password hashes.
- Limited Access: Only protect the necessary resources with Basic Authentication. Avoid applying it globally if not needed.
- Rate Limiting: Implement rate limiting to prevent brute-force attacks, where an attacker repeatedly tries different username/password combinations.
- External Authentication: Consider using an external authentication provider to manage users and credentials if possible. This can offload some of the security responsibilities. By understanding how HTTP Basic Authentication works and following these best practices, you can improve the security of your APIs and web applications.
Security Considerations for Basic Authentication#
While Basic Authentication is a convenient tool, it’s important to know its security limitations and take steps to mitigate risks.
| Risk | Mitigation |
|---|---|
| Eavesdropping: Since credentials are only Base64 encoded, not encrypted, they can be intercepted during transmission. | Always use HTTPS to secure the communication channel between the client and server. Zuplo enforces HTTPS by default for all API traffic. |
| Brute-Force Attacks: Attackers can try to guess usernames and passwords by systematically trying different combinations. | Implement rate limiting to restrict the number of authentication attempts from a single IP address within a given time frame. Zuplo offers rate-limiting features to help protect against such attacks. |
| Credential Replay: If an attacker captures the Authorization header, they can replay it to gain unauthorized access. | Consider using short-lived access tokens instead of long-lived passwords. This way, even if a token is compromised, its window of vulnerability is limited. |
| No Built-in Logout: Basic Authentication has no standard mechanism for explicitly logging out a user. | In the context of APIs, you can implement a token revocation mechanism where tokens can be invalidated or have their expiration shortened if needed. |
These vulnerabilities highlight the need for careful consideration when using Basic Authentication and implementing suitable safeguards to mitigate potential risks. While Basic Authentication might not be suitable for highly sensitive data or complex authorization scenarios, it remains a practical solution for situations where simplicity and ease of implementation are priorities.
Basic Authentication using Zuplo#
Zuplo streamlines the process of adding Basic Authentication to your APIs. Basic authentication can be added to your Zuplo APIs by going to the Code tab in the Zuplo dashboard and opening the routes.oas.json file.
In the routes.oas.json file, open the endpoint you want to add auth to and click Add Policy under Request.
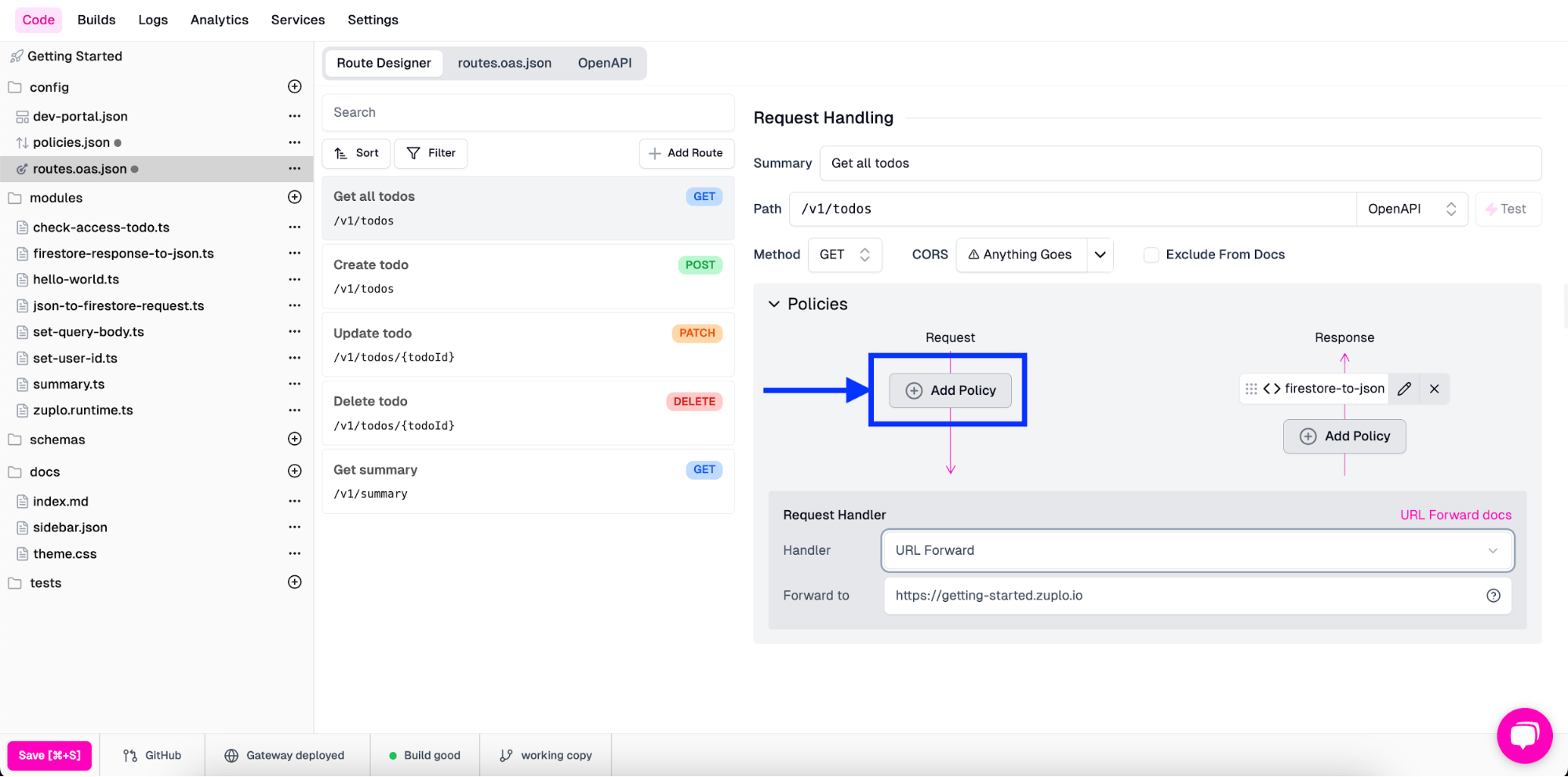
On the Choose Policy modal, select Basic Auth.
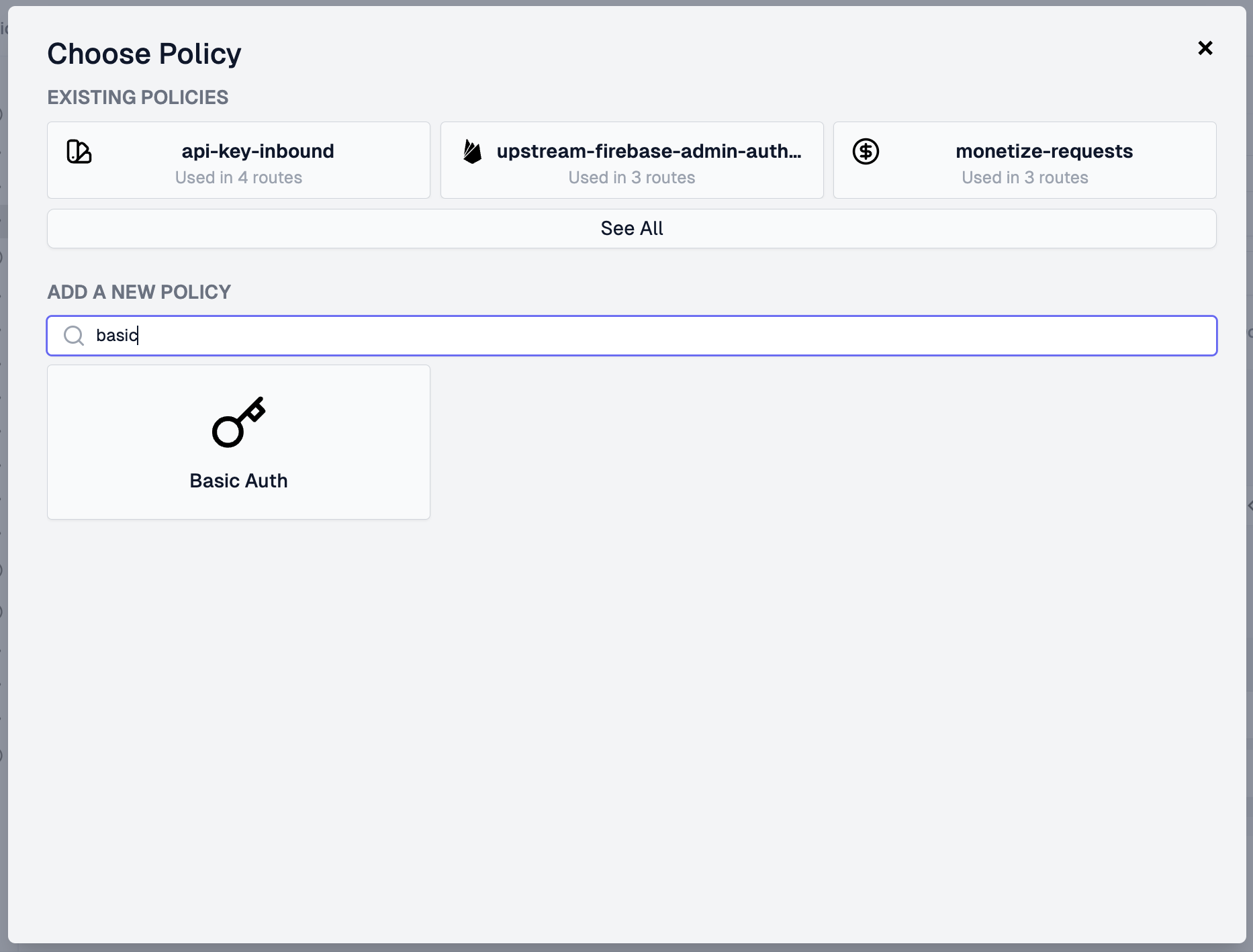
On the Create Policy modal, enter your configuration, including the usernames and passwords of users you'd like to give API access to. Once you've completed this, click OK.
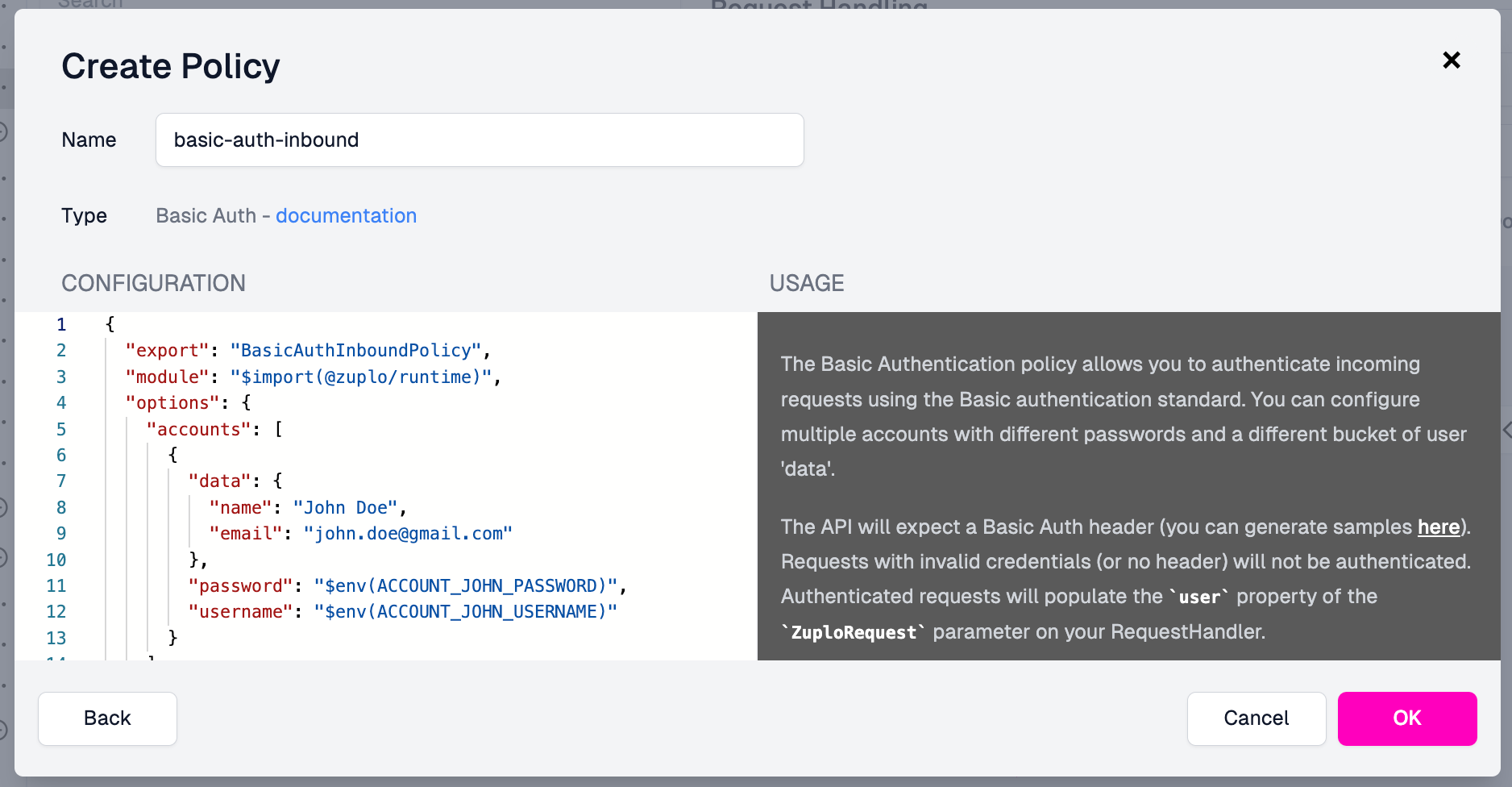
Then, ensure that the policy is in the request pipeline where you want it. If this is the only policy in the pipeline, you're set! If there are multiple, ensure you've got it in the proper order, likely as the first policy to execute in the request pipeline.
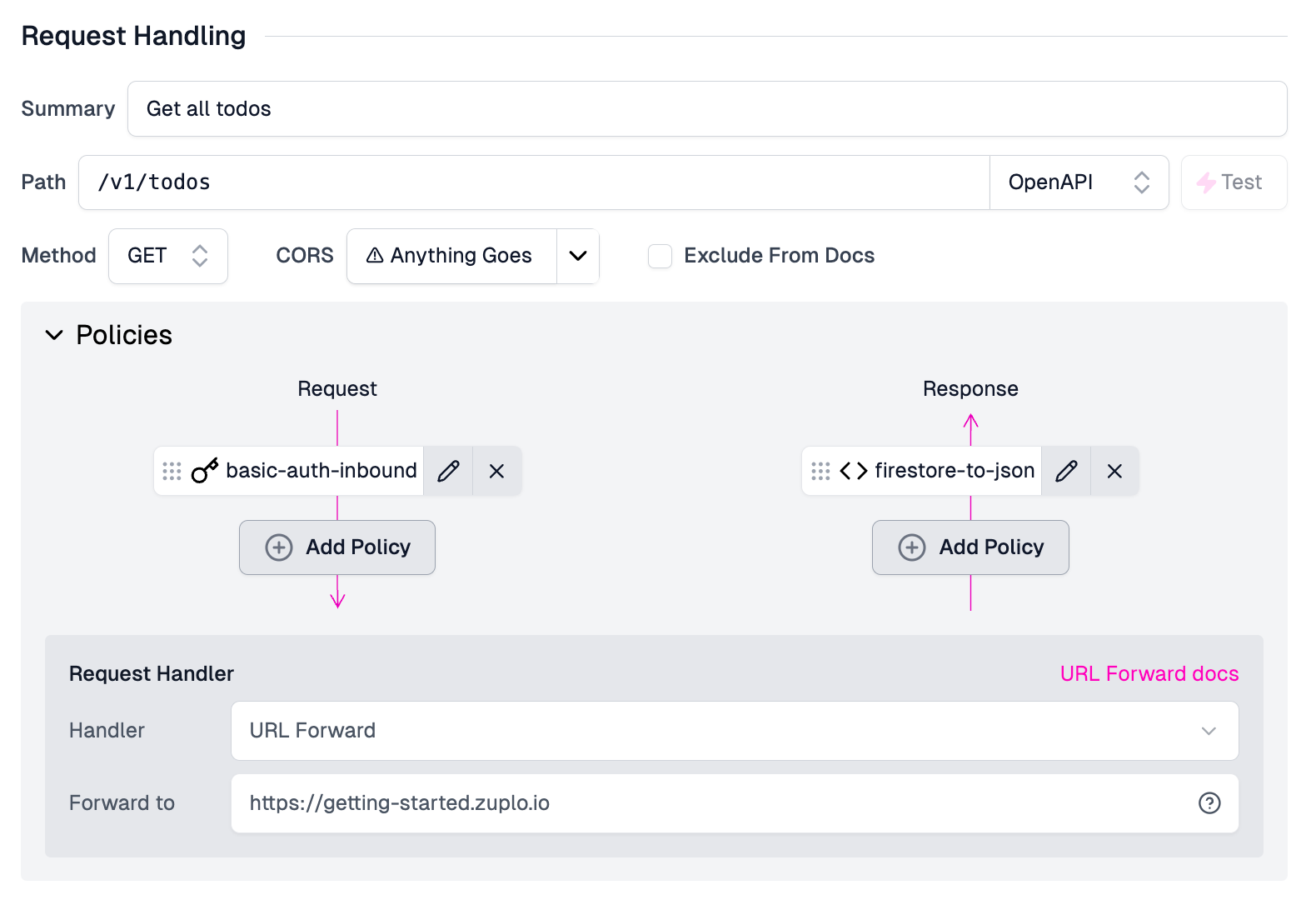
Lastly, Save your configuration and deploy your updated API. Zuplo will handle the authentication challenge/response flow and credential validation. It's that easy!
Conclusion#
HTTP Basic Authentication, despite its simplicity, is still a relevant and practical solution for securing APIs, particularly when you need a lightweight, easy-to-implement mechanism. While it may not be as feature-rich as modern authentication methods, understanding how it works and following security best practices can make it an effective tool for protecting your resources. Using a secure connection (HTTPS/TLS) is crucial to protect credentials when using Basic Authentication. Zuplo simplifies the implementation of Basic Authentication, allowing you to add this security layer effortlessly. By leveraging Zuplo’s capabilities and following the recommendations in this guide, you can enhance the security of your APIs without sacrificing simplicity or ease of use. Sign up for Zuplo today to add Basic Auth to your APIs in minutes.









