How RBAC Improves API Permission Management
Role-Based Access Control (RBAC) simplifies API permission management by assigning users to predefined roles, each with specific permissions. This approach ensures users only access what they need, reducing security risks and administrative workload. Here's what you need to know:
-
Key Benefits of RBAC:
- Strengthens security with precise access control.
- Simplifies permission management by grouping permissions into roles.
- Scales easily with organizational growth.
- Meets compliance requirements with clear audit trails.
-
How RBAC Works:
- Define roles based on job functions.
- Use an API gateway (ex. Zuplo) to automate enforcement across your API endpoints.
- Test policies to ensure proper access control.
RBAC ensures your API ecosystem stays secure, manageable, and scalable while minimizing risks and supporting compliance. Keep reading to learn how to implement and optimize RBAC for your organization.
RBAC Explained: How it works and when to use it#
In case that explanation of RBAC above wasn't enough for you - here's our friend Erik Wilde to explain it.
Steps to Implement RBAC for API Permission Management#
Defining Roles and Permissions#
Start by aligning roles with the principle of least privilege. This means mapping roles to specific job functions and granting only the permissions necessary for users to perform their tasks. The goal is to create a structure that minimizes unnecessary access while ensuring users can do their jobs efficiently.
Here are some key points to consider when designing roles:
- Align roles with organizational responsibilities.
- Use detailed permission controls to limit access.
- Ensure duties are separated to avoid conflicts.
- Create clear patterns for role inheritance.
- Design roles that can scale with organizational growth.
For a concrete example - here is how we defined roles within Zuplo.
- Admin: Admins have full access to the account and can manage all aspects of the account, including billing, members, and roles.
- Developer: Developers can create and manage projects and environments in the account. Developers can edit preview and development resources, but not production resources.
- Member: Members of an account don't have any account level or project level permissions. Members can be granted project level permissions by an admin.
As you can see, Admin is a superset of Developer, which is a superset of Member. The member role follows the least privilege principle.
Once you've defined the roles, use API management tools to enforce these rules automatically through policy middleware.
Integrating RBAC with API Management Tools#
For a developer-friendly setup, tools like Zuplo offer code-first solutions for implementing RBAC. Here's the high level steps to integrate RBAC into your API:
- Set up authentication methods (e.g., JWT, API keys, or mTLS).
- Use policy middleware to define and enforce permissions.
- Add role guards to secure specific API endpoints.
Testing and Validating RBAC Policies#
After setting up RBAC, thorough testing is essential to ensure everything works as expected. Testing helps identify any gaps or conflicts in permissions.
Steps for effective testing:
- Document scenarios: Create a detailed list of role-endpoint combinations, including overlaps in permissions.
- Automate tests: Use automated tools to validate role-based access to endpoints.
- Monitor performance: Use RBAC-specific analytics to track how well the policies are working and make adjustments as needed.
Tutorial: Implementing RBAC for APIs#
Here's a quick tutorial on building a simple RBAC system on top of your API using the step from above. I'm going to use Zuplo for this, but the same concepts will apply regardless of your tooling.
1. Add Authentication to Your API#
If you API doesn't already have an authentication method like API Key Authentication or Basic Authentication - you definitely need it before implementing RBAC. The authentication layer will tell us who is calling our API. There are various identity providers you can use to manage all of your API customers - but we're going to stick with API key authentication to keep things simple.
Spin up a Zuplo project and
select our Todo List API sample so we have some real data. Once your project is
ready, head over to the Code tab and open routes.oas.json.
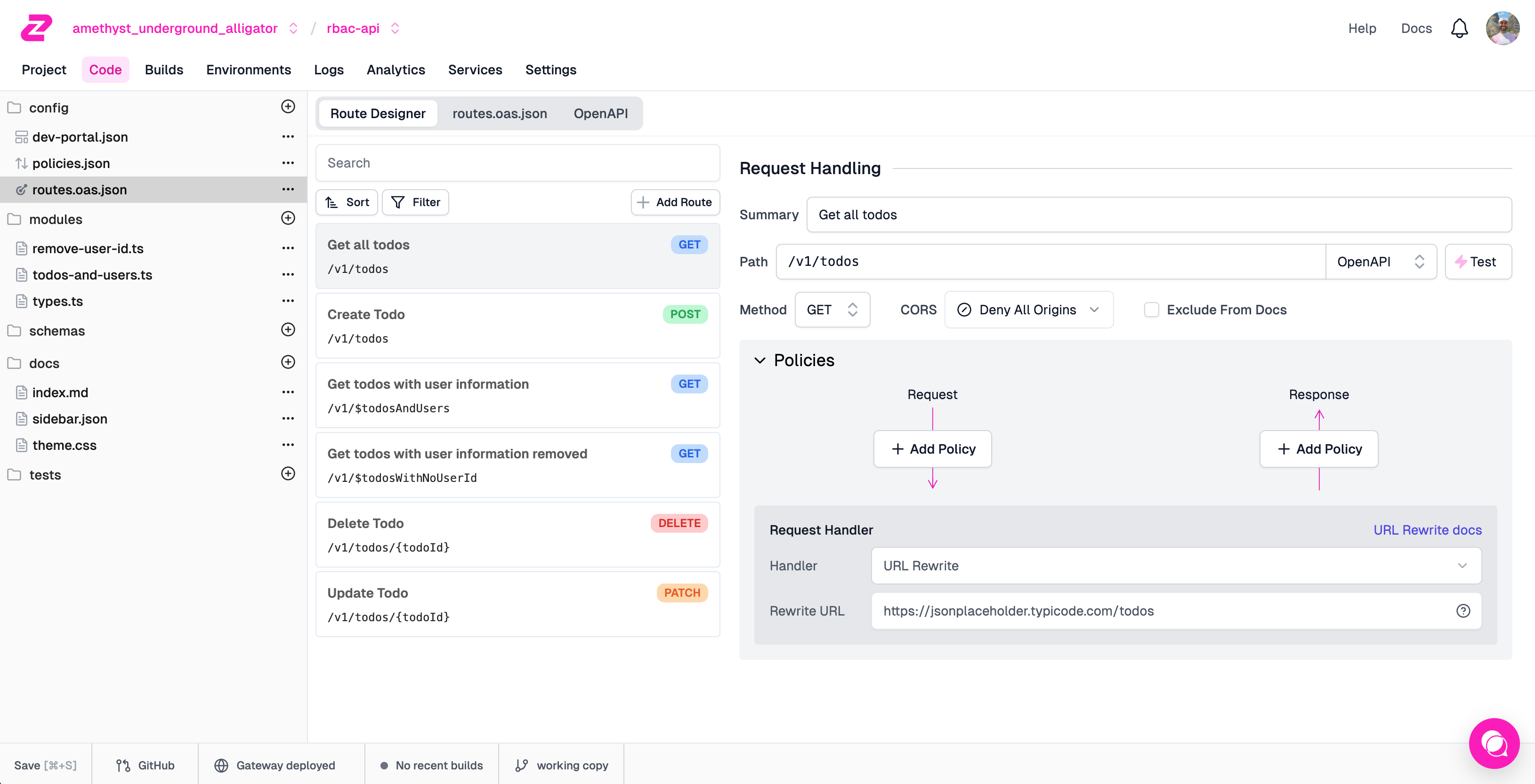
The "Get all todos" endpoint is simply proxying the jsonplaceholder API on the
path /v1/todos. Now, let's add authentication.
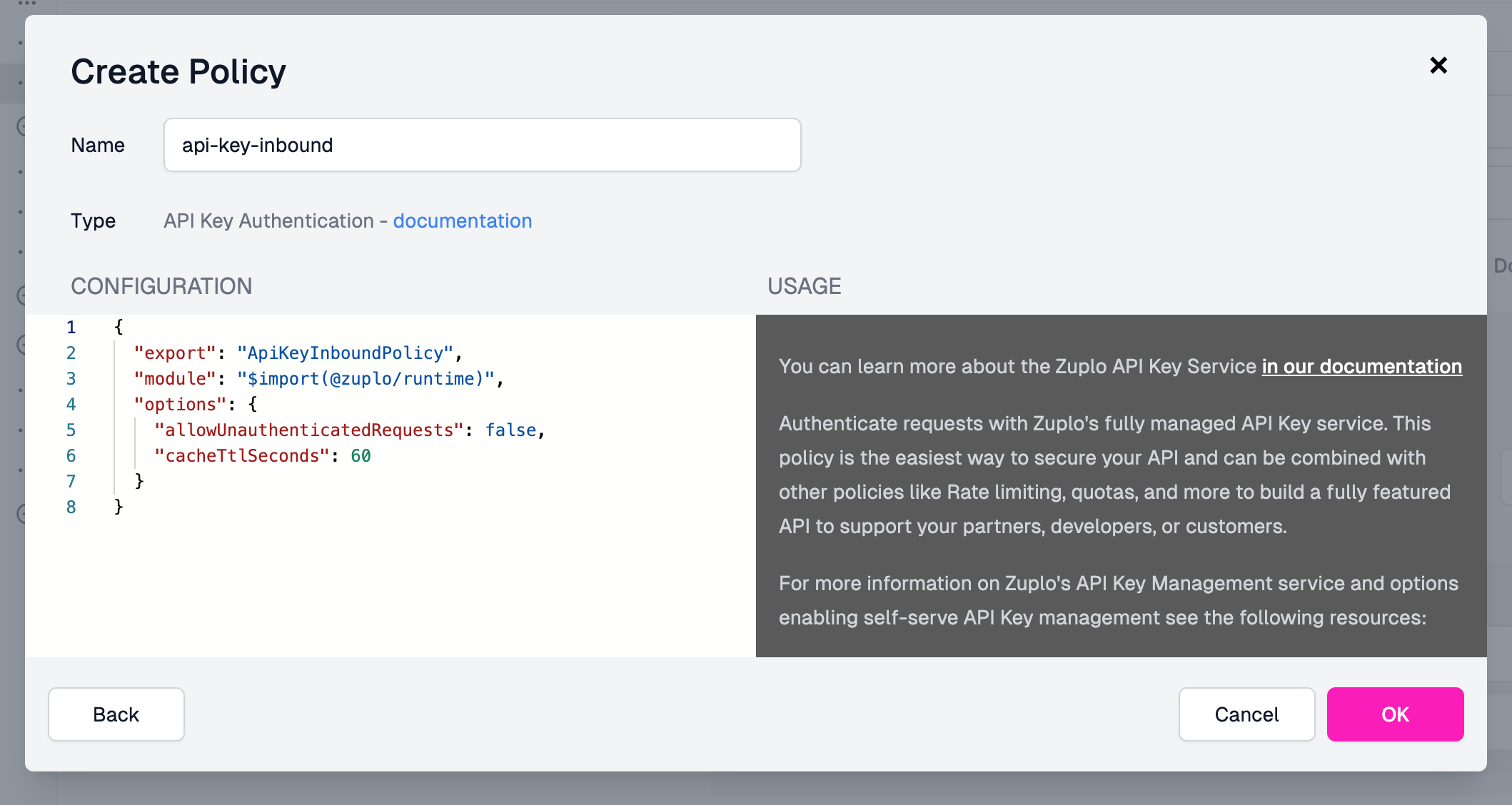
Click the Add Policy button and select API Key Authentication. The default configuration is fine so go ahead and click OK.
After you Save you changes, click Test to pop open the test console. If you fire a request off you'll notice we have a 401 error now.
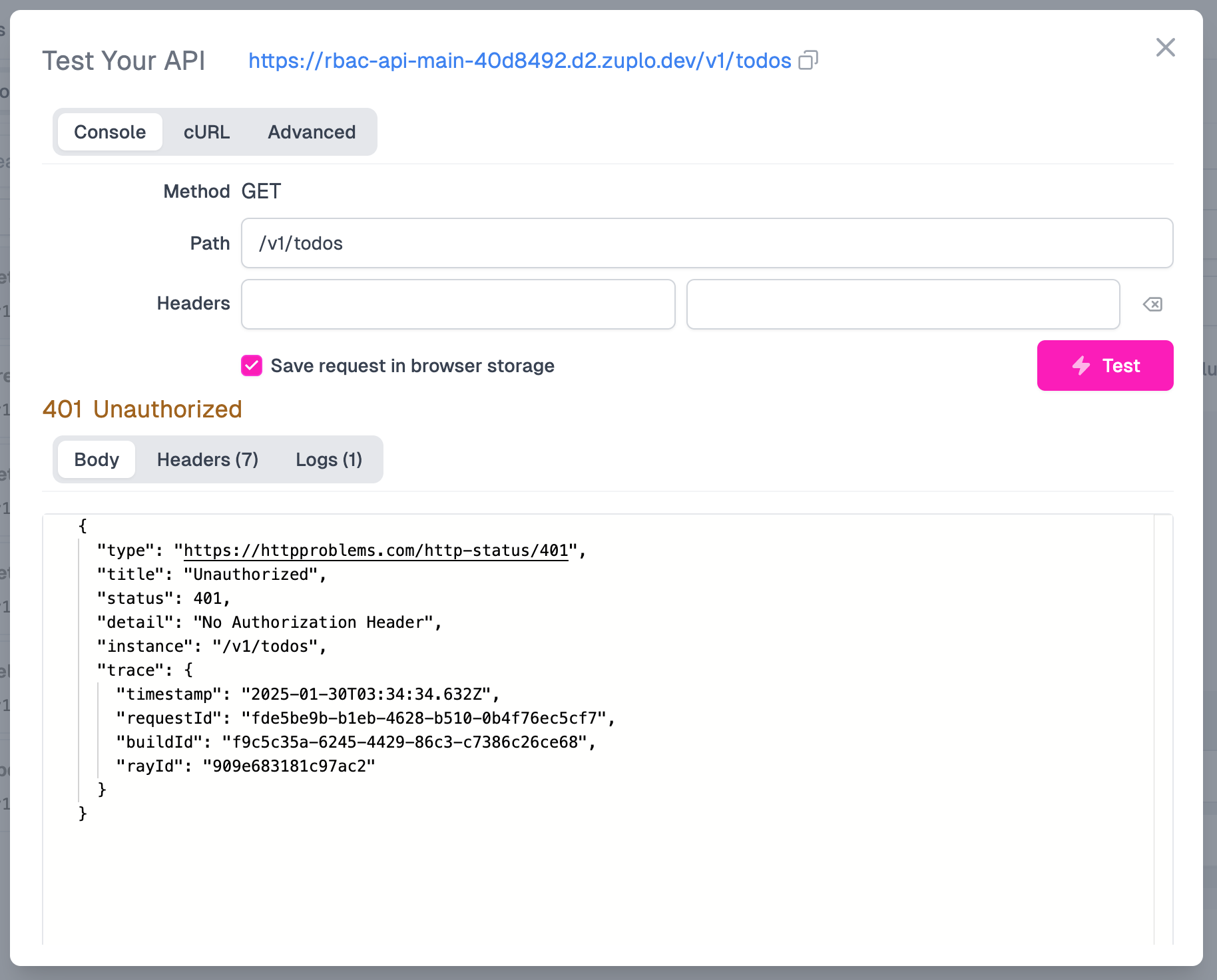
This error is actually good news - it means our policy is running and rejecting unauthenticated requests. Now let's listen to the error and get ourselves some credentials for the authorization header.
Hop over to the Services tab and click Configure on the API Key Service.
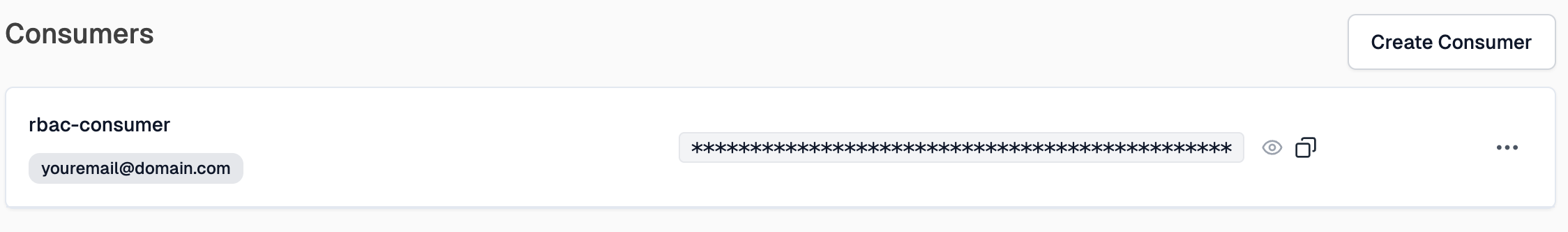
We need to create a trusted consumer for our API that we can issue API keys
to. Click Create Consumer and match this setup:
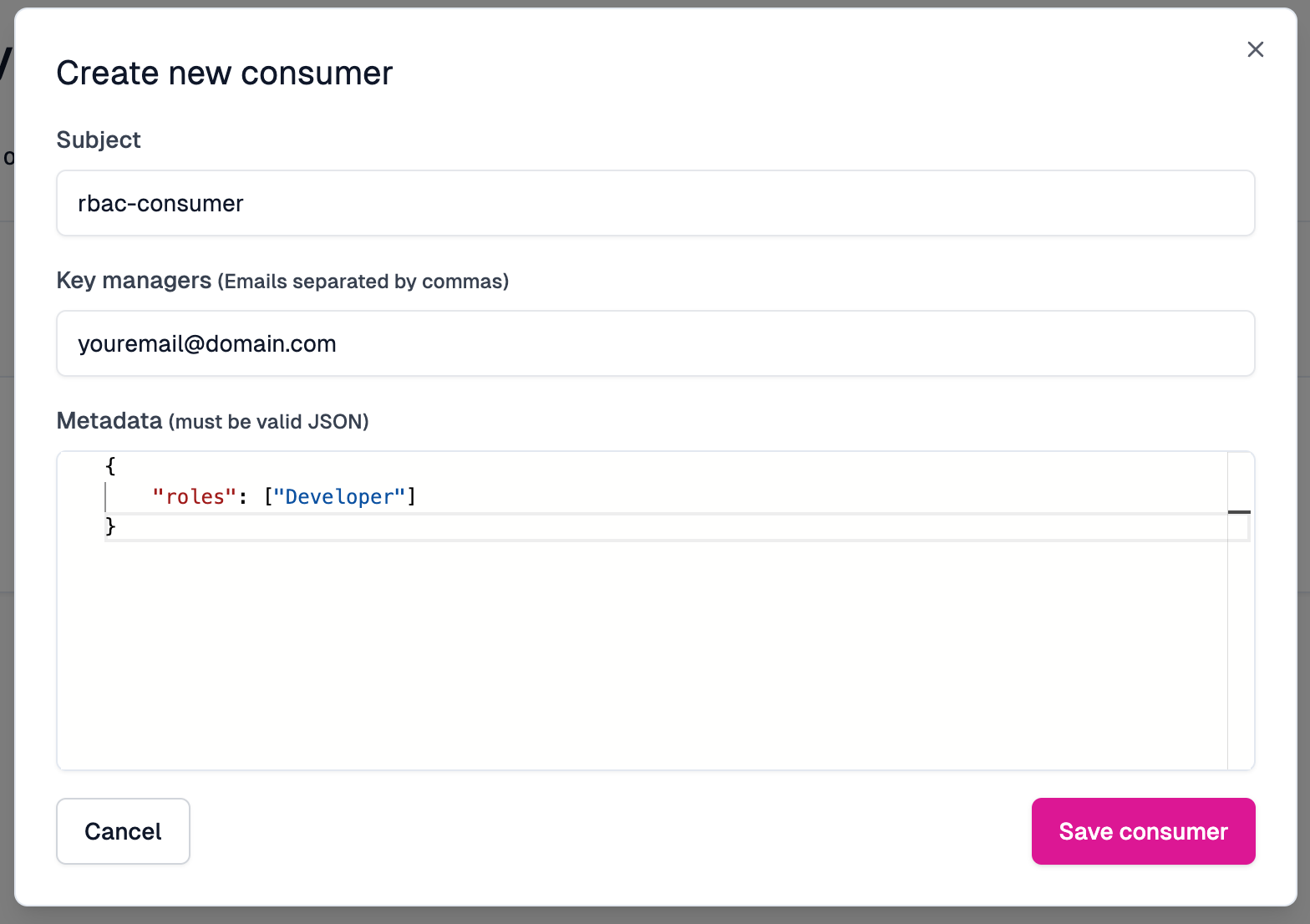
We are going to store our RBAC role in the consumer's metadata and read it at runtime to determine if this consumer can access our endpoint. Click Save Consumer and copy the API key.
Now head back to the Code tab > routes.oas.json > Get all todos. Pop open
the Test console again and fill in the authorization header as follows:
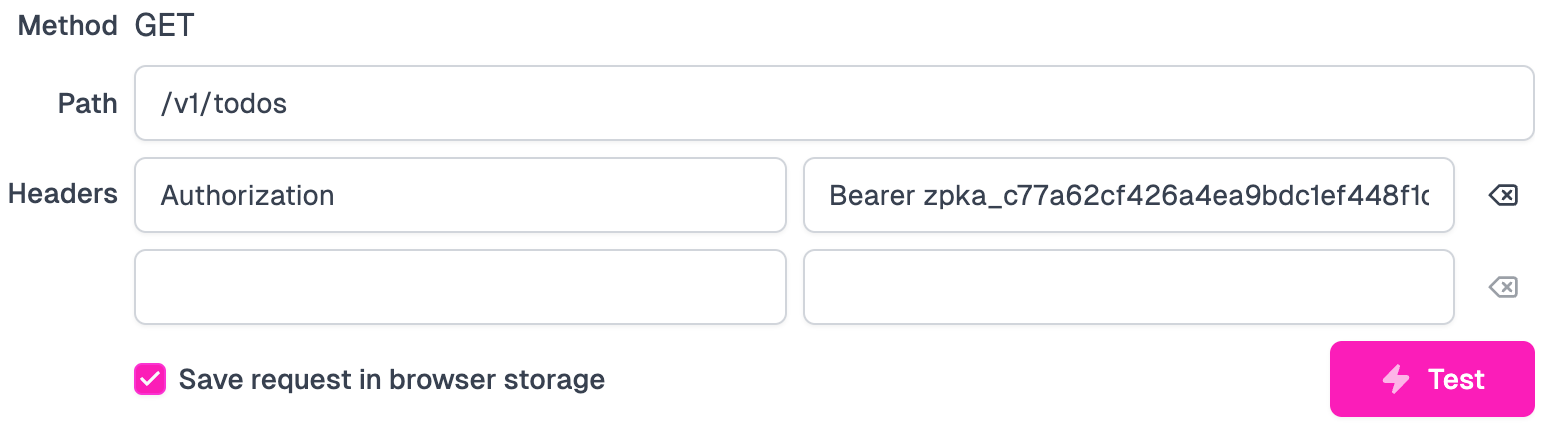
The format is Bearer <YOUR_API_KEY>. Now if you click Test we'll get a
200! We are now authenticated!
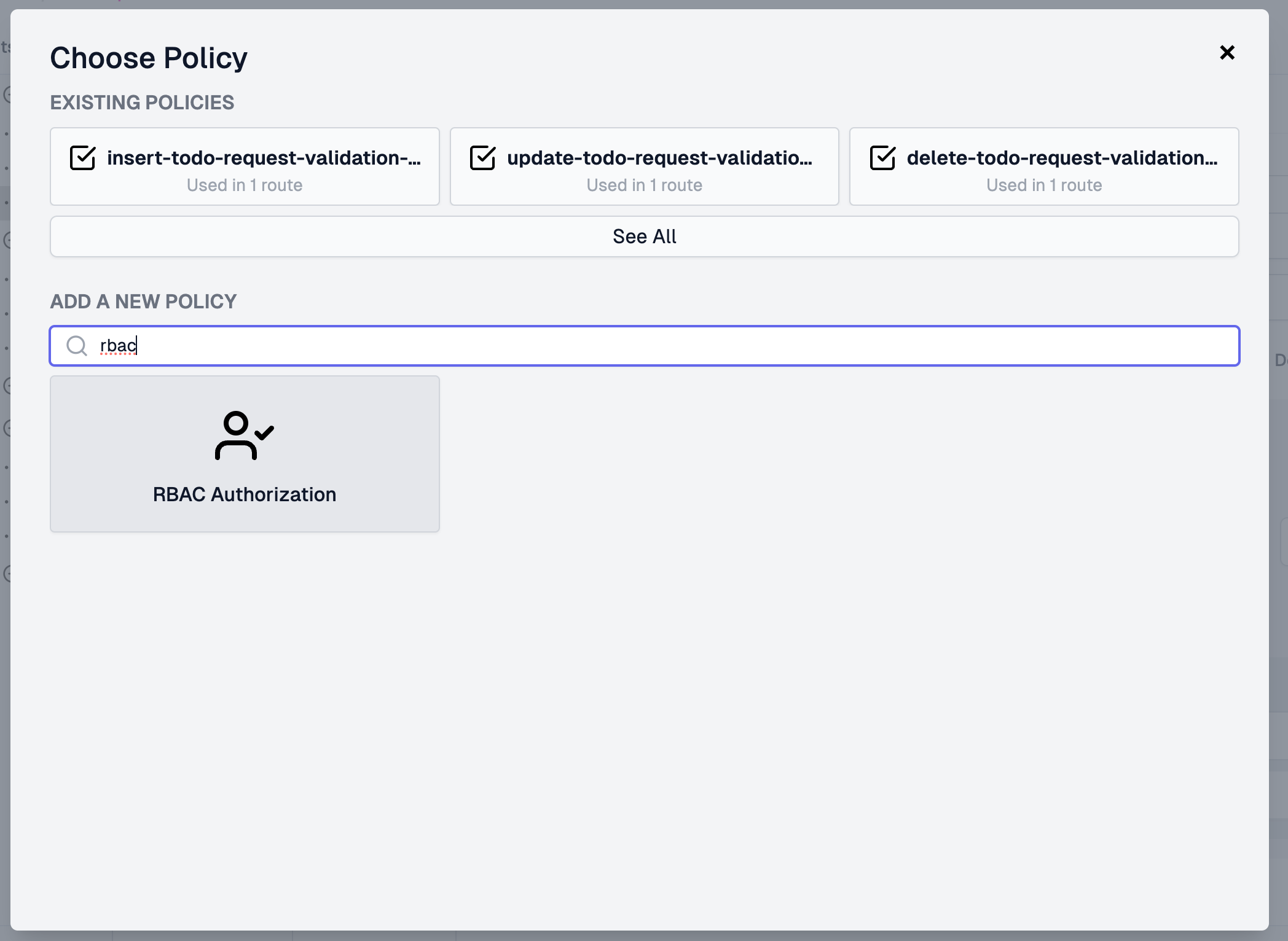
2. Add RBAC to Your API#
Authentication is just the first step. Now that we know who is calling our
API, we need to know what they are allowed to access (ie. Authorization). To
do this, we are going to add another policy after our authentication step to
check the roles metadata we added in the last step. Click Add Policy and
search for RBAC.
We find that RBAC implementations tend to vary across organizations - so instead of providing a simple plugin like we did with API key authentication - we are providing you a code template you can customize!
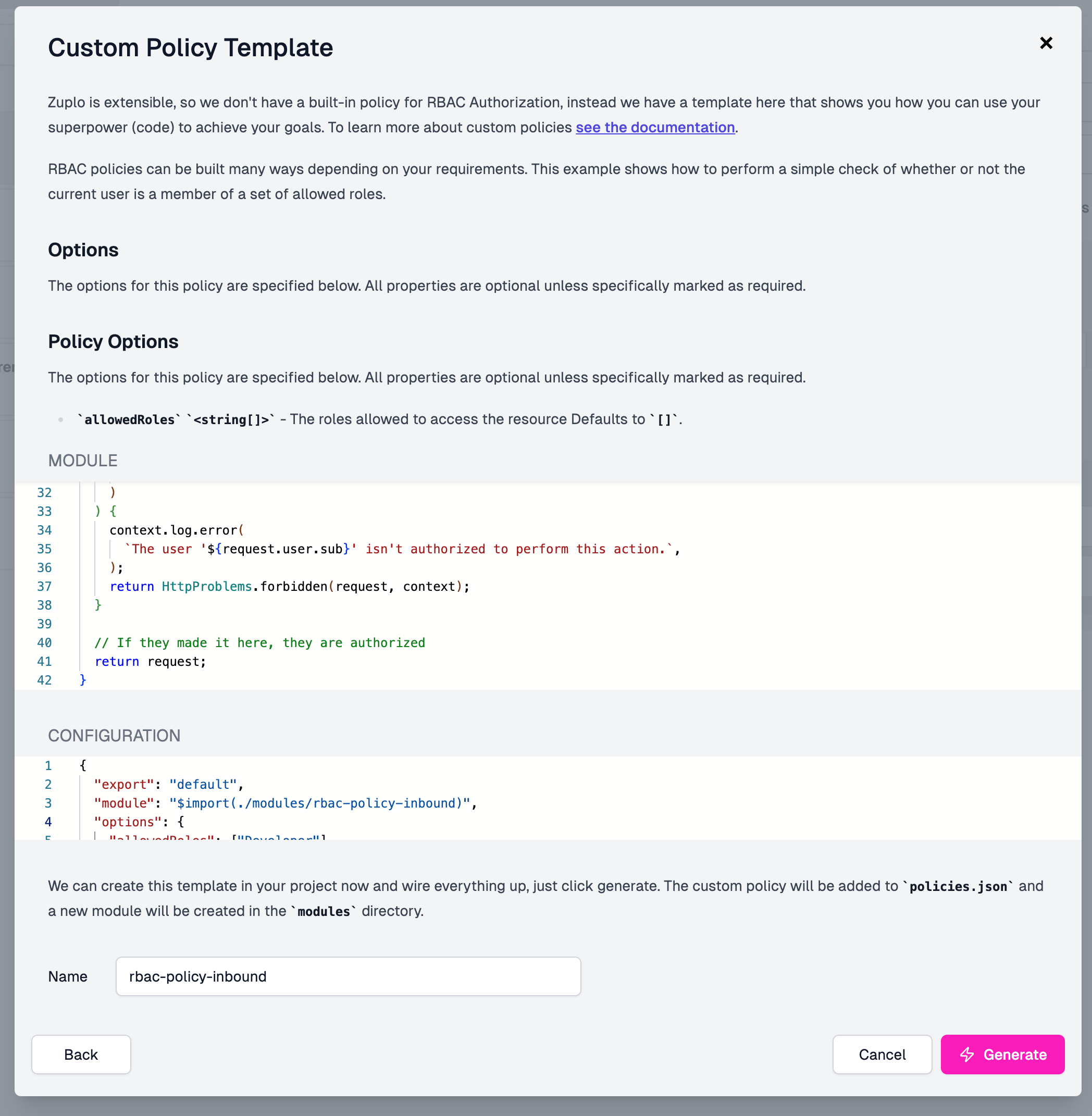
Here's the code in case you want to implement this yourself
import { HttpProblems, ZuploContext, ZuploRequest } from "@zuplo/runtime";
interface PolicyOptions {
allowedRoles: string[];
}
export default async function (
request: ZuploRequest,
context: ZuploContext,
options: PolicyOptions,
policyName: string,
) {
// Check that an authenticated user is set
// NOTE: This policy requires an authentication policy to run before
if (!request.user) {
context.log.error(
"User isn't authenticated. A authorization policy must come before the RBAC policy.",
);
return HttpProblems.unauthorized(request, context);
}
// Check that the user has roles
if (!request.user.data.roles) {
context.log.error("The user isn't assigned any roles.");
return HttpProblems.unauthorized(request, context);
}
// Check that the user has one of the allowed roles
if (
!options.allowedRoles.some((allowedRole) =>
request.user?.data.roles.includes(allowedRole),
)
) {
context.log.error(
`The user '${request.user.sub}' isn't authorized to perform this action.`,
);
return HttpProblems.forbidden(request, context);
}
// If they made it here, they are authorized
return request;
}Under Policy Option you'll see we mention a allowedRoles option - this
will be an array of roles that are authorized to access this endpoint. Within
the Configuration section - let's add the Developer role from earlier. You
can just paste the following in, in case editing JSON configuration makes you as
nervous as me.
{
"export": "default",
"module": "$import(./modules/rbac-policy-inbound)",
"options": {
"allowedRoles": ["Developer"]
}
}Click Generate and then Save your new policy. Now let's Test it out to see if it works.
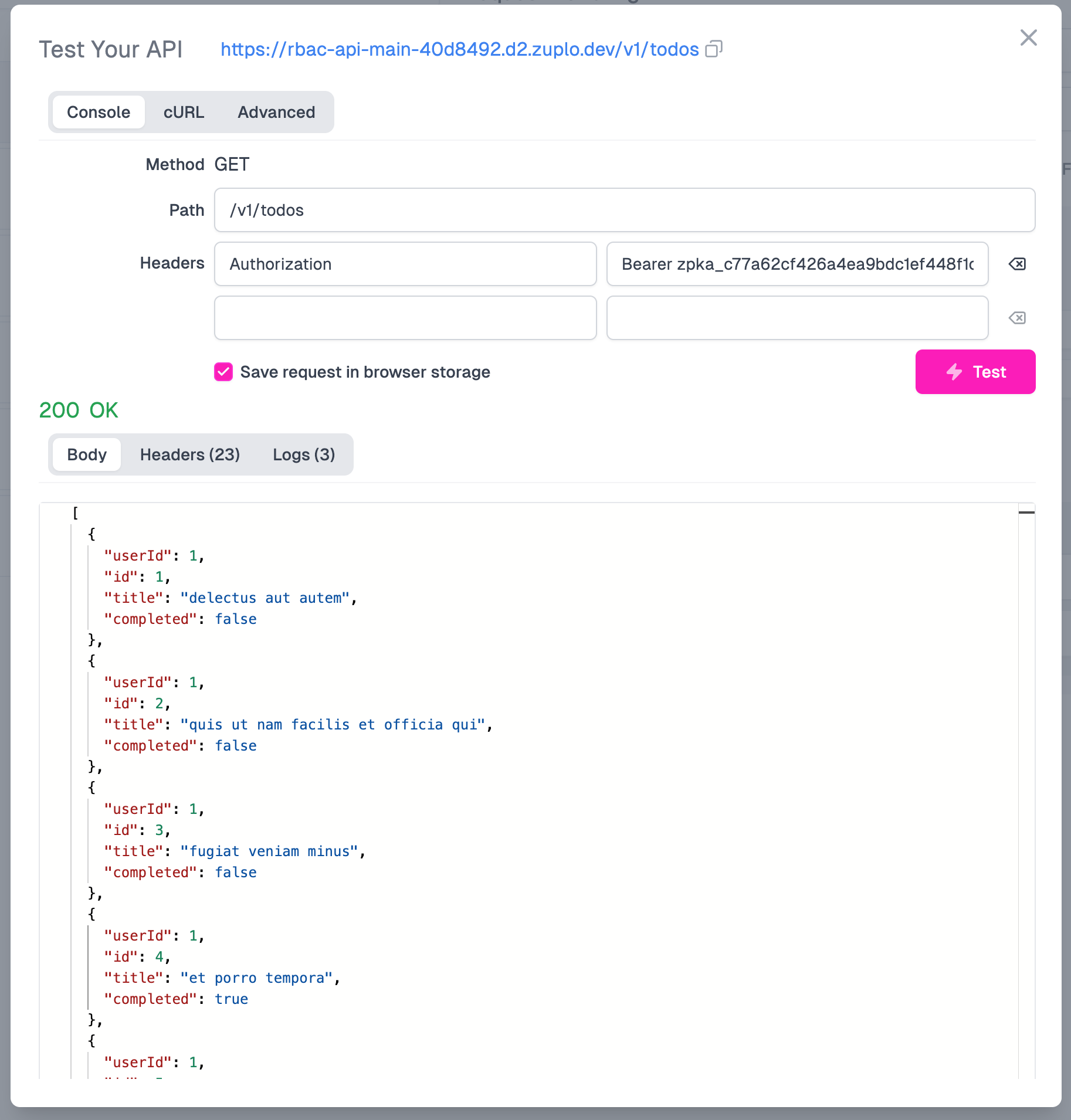
Nice - we are now enforcing roles.
3. Revoking Access#
As great as seeing a 200 response is - we need to follow our own advice here and
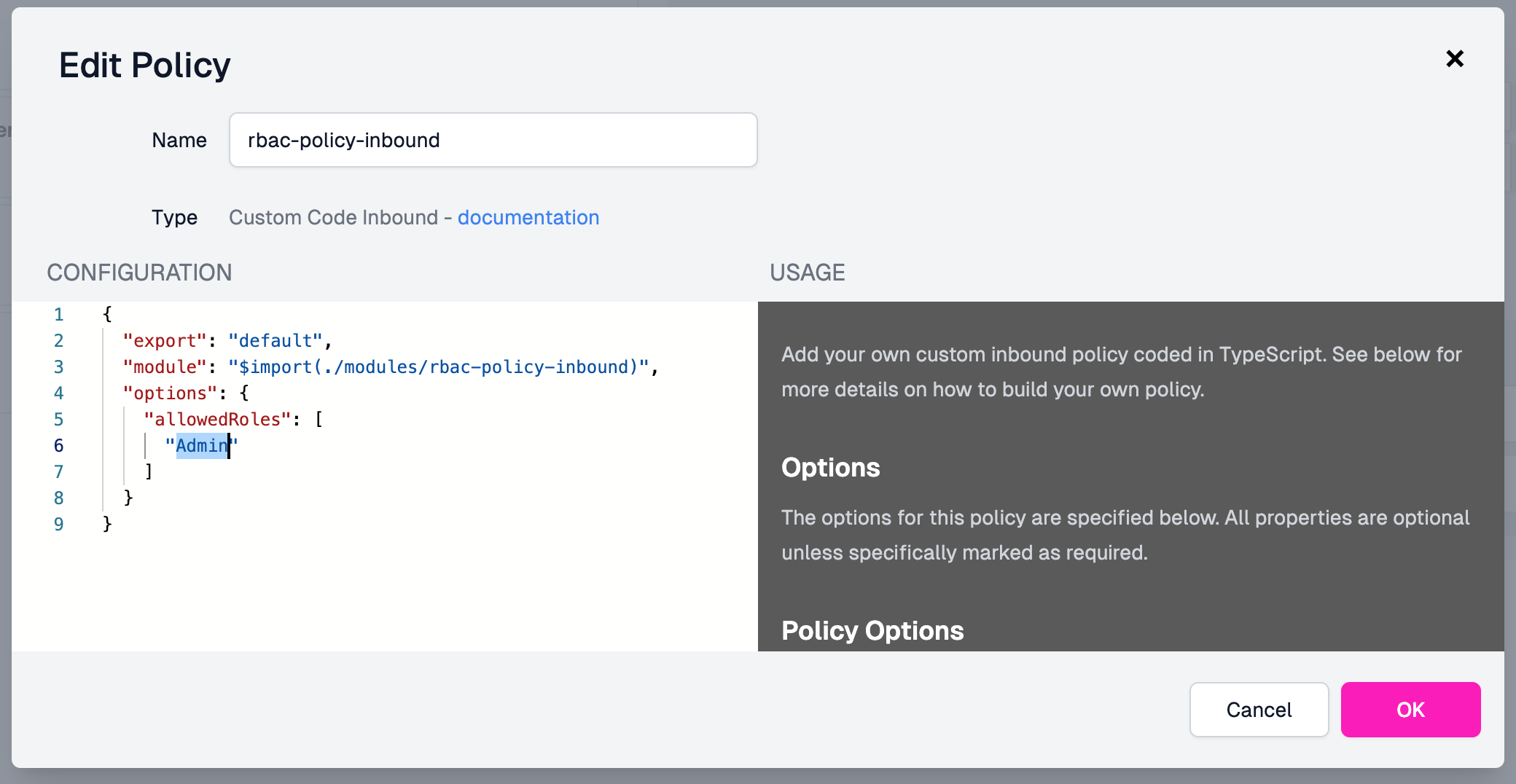
validate the policy is working as expected. To do that, click the pencil icon
next to the rbac-policy-inbound policy to edit it. Let's make it so only users
with the Admin role can access this endpoint. Change Developer to Admin,
click OK and then Save your change.
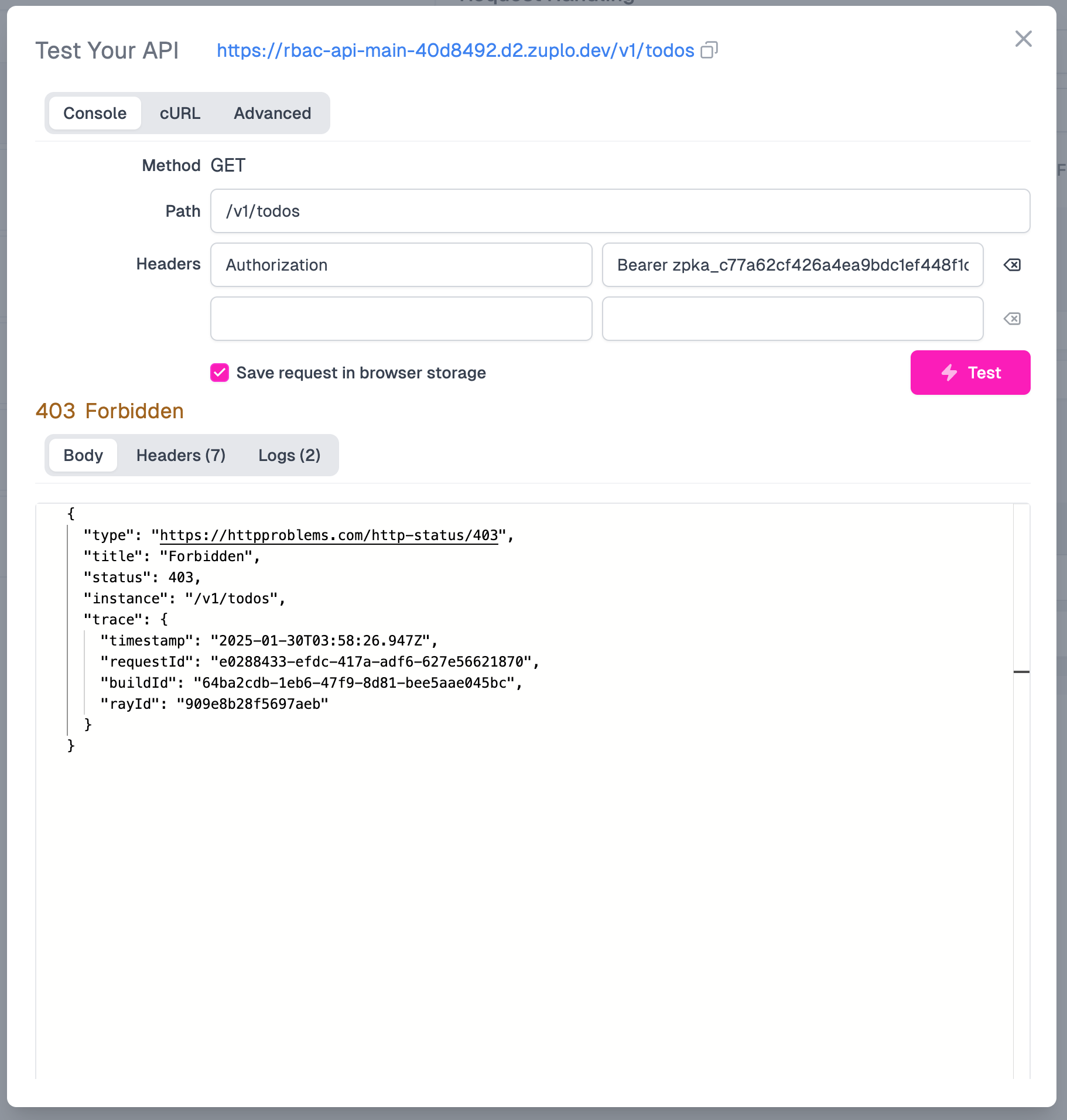
If we try calling our API again from the Test tab - we now receive a
403 Forbidden error. Whomp whomp! But hey - at least we have a working RBAC
implementation on our API now.
Advantages of Using RBAC in API Permission Management#
Strengthening Security with Precise Access Control#
RBAC improves API security by enforcing the principle of least privilege. This means users are granted only the permissions necessary for their specific role. By limiting access to what's essential, RBAC minimizes the risk of unauthorized access while ensuring smooth operations.
Making Permission Management Easier and Scalable#
Managing permissions becomes much simpler with RBAC, especially during organizational shifts or team growth. Instead of assigning permissions to each individual, administrators can use predefined role templates to manage access efficiently.
As teams grow, new roles can be added or adjusted without interfering with existing systems.
| Traditional User Management | RBAC Approach |
|---|---|
| Assign permissions individually | Assign permissions by role |
| Modify permissions manually | Transition roles seamlessly |
| Complexity grows with user count | Complexity stays stable with roles |
| High workload (manual handling) | Lower workload (standard roles) |
Meeting Compliance and Audit Requirements#
RBAC's structured approach to access control helps meet compliance standards by offering clear and traceable permission management. During audits, development teams can easily present evidence of compliance through well-documented access logs and permission changes.
Key audit-friendly features of RBAC include:
- Automated role change tracking
- Permission usage reports
- Access attempt logs
- Tools for verifying compliance

Over 10,000 developers trust Zuplo to secure, document, and monetize their APIs
Learn MoreTips for Effective RBAC Management in APIs#
Regularly Review and Update Roles#
Keeping roles up-to-date is essential for maintaining an efficient RBAC system. Schedule quarterly reviews to ensure permissions align with your organization's current needs. During these reviews, document key details such as:
- Active roles and their associated permissions
- Relationships between users and roles
- Patterns in permission usage
- Changes made to roles recently
Automate Role Assignments#
Managing roles manually can quickly become overwhelming as your organization grows. By integrating your RBAC system with identity providers, you can automate user-role assignments. This not only reduces the workload for administrators but also helps minimize mistakes in assigning permissions.
Leverage API Management Platforms for RBAC#
Enhance your RBAC system by pairing automated role management with API management tools. Platforms like Zuplo simplify this process by using policy-first API gateways that enforce RBAC directly through code.
Look for tools that offer features like policy-as-code, real-time analytics, and seamless integration with identity systems. These capabilities help keep your RBAC system organized as your organization scales.
Conclusion: The Importance of RBAC in API Permission Management#
Role-Based Access Control (RBAC) helps simplify administration and improve security by limiting access to only what’s necessary [1][3]. By defining roles and automating assignments, teams can maintain consistency and streamline operations. This structured method not only supports compliance with audit-ready frameworks but also prevents unauthorized access through centralized role controls, making it scalable for growing organizations.
Many platforms include features designed to boost API security and management [1]. Following the best practices discussed earlier can help teams build a resilient and efficient API ecosystem.
Implementing RBAC ensures that API permission systems stay secure, efficient, and well-suited to evolving organizational needs. If you'd like to implement RBAC on your API sign up for a Zuplo account today and discover how easy it is to secure your APIs with our developer-first API management platform.
FAQ on RBAC for APIS#
1. What is RBAC and why is it important for API security?#
Role-Based Access Control (RBAC) is a permission management methodology that assigns privileges to users based on their roles. In the context of APIs, RBAC helps enforce strict authorization rules, ensuring that each user or service only accesses the resources necessary for their function. This approach reduces the risk of unauthorized access and data breaches.
2. How does RBAC differ from other access control models like ABAC or ACLs?#
- RBAC (Role-Based Access Control): Grants access based on user roles.
- ABAC (Attribute-Based Access Control): Uses user attributes (e.g., department, location) to make authorization decisions.
- ACLs (Access Control Lists): Assign permissions to specific resources
directly for each user or user group.
RBAC is often simpler to manage at scale because administrators can assign or revoke roles rather than modifying individual permissions for each user.
3. What is the difference between authentication and authorization in an API context?#
- Authentication verifies the identity of the user or system (e.g., using username/password, tokens).
- Authorization determines which resources or operations the authenticated
user is allowed to perform (e.g., based on RBAC roles).
In short, authentication answers “Who are you?” while authorization answers “What can you do?”
4. Is RBAC enough for modern API security, or do I need additional measures?#
While RBAC is a foundational authorization mechanism, you often need additional layers for comprehensive API security. These may include multi-factor authentication (MFA), API gateways with rate limiting, encryption in transit (TLS/SSL), logging and monitoring of API requests, and regular security audits to detect vulnerabilities.
5. Can I combine RBAC with OAuth 2.0 or JWT-based authentication?#
Yes. Typically, OAuth 2.0 or JWT tokens handle authentication and basic authorization scopes. You can store user roles as claims within the JWT or fetch them from a central user directory. When an API receives a token, it can verify the claims and map them to RBAC roles to enforce fine-grained access controls.
6. How do I manage user roles and permissions dynamically?#
Most identity and access management (IAM) systems or directory services allow you to update user roles in real-time. You can integrate these systems with your API to fetch the latest role assignments for each user on every request. Some APIs also cache role information temporarily for performance, but you need a strategy to refresh this cache when roles change.
7. What are the common pitfalls when setting up RBAC for APIs?#
- Overly broad roles: Roles with too many permissions defeat the purpose of RBAC.
- Lack of documentation: Confusion arises if roles and permissions aren’t clearly defined and documented.
- No regular reviews: Neglecting to review role assignments and permissions can leave outdated access rights in place.
- Inconsistent enforcement: If RBAC checks are enforced inconsistently across endpoints, gaps in security may emerge.
8. How can RBAC help with regulatory compliance?#
RBAC can simplify audits by clearly documenting who has access to what. Many regulations (such as GDPR, HIPAA, PCI DSS) require demonstrating that only authorized individuals can access sensitive data. RBAC’s structured approach to permission management makes it easier to produce audit logs and comply with these regulations.
9. How do I test my RBAC rules to ensure they’re secure?#
- Unit Tests: Validate that each API endpoint enforces role checks.
- Integration/End-to-End Tests: Simulate real-world scenarios with different user roles and permissions.
- Penetration Testing: Hire security experts or use tools to test whether roles can be bypassed or escalated.
- Regular Audits: Periodically review role assignments and adjust permissions as business needs change.
10. Does RBAC scale for microservices architectures?#
Yes, RBAC can scale across microservices, but it requires consistent identity and access management across all services. You can use a centralized IAM solution or API gateway to distribute and enforce RBAC rules uniformly, ensuring that each microservice trusts the same source of user roles and permissions.
11. Can RBAC be used with Zero Trust security models?#
Absolutely. Zero Trust models dictate that no user or system is inherently trusted. RBAC can be integrated by continuously verifying user roles and permissions for every request, aligning with Zero Trust principles where every access request is vetted and minimized.









