Protecting Your APIs from Insider Threats: The Access Control Playbook
Here's something we don't talk about enough: while you're busy building firewalls against outside attackers, your biggest API security risks might be sitting in your team meetings. We're talking about insider threats — those security headaches that come from people who already have legitimate access to your systems. And they're not always the villains you might imagine.
Let's talk numbers for a second. A whopping 81% of data breaches involve misused credentials. Three-quarters of your users probably have more access than they need, and half admit to sharing their credentials with others. Yikes.
But don't panic — with some smart access control strategies, you can lock things down without making your developers hate their lives. Let's dig into how you can protect your APIs from the inside out.
- Why Insider Threats Are Different in API Environments
- The Tell-Tale Signs: Identifying Suspicious Behavior Patterns
- Building Your Defense: Core Security Principles
- Advanced Monitoring Strategies
- Your API Protection Action Plan: From Detection to Response
- Future Trends: The Evolving Landscape of API Security
- The Path Forward: Securing Your APIs from the Inside Out
Why Insider Threats Are Different in API Environments#
Traditional security is all about building walls — firewalls, intrusion detection, the works. But APIs change the game completely, and you need different tactics to keep them safe.
Credential-Based Access Creates New Vulnerabilities#
In the old days, insider threats meant someone physically accessing a database or downloading files. With APIs, it's all about those keys, tokens, and authorizations that work across multiple systems. Understanding different API authentication methods is crucial because one compromised credential and suddenly someone has the keys to your entire digital kingdom.
Machine-to-Machine Communications#
Traditional security watches what humans do — when they log in, what files they access. But with APIs, you've got machines talking to other machines, often using authentication methods like JWT or API Key authentication. How do you spot trouble when most of the conversations aren't even involving humans directly? It's like trying to eavesdrop on robots.
Distributed Attack Surface#
Each API endpoint is another potential door into your systems. And let's be honest — how many endpoints do you have now? Dozens? Hundreds? Thousands? That's a lot of doors to keep locked, and it only takes one careless developer with too much access to create a security nightmare.
The old security playbook just doesn't cut it anymore. Looking for weird login times or suspicious file downloads won't catch API-specific threats. You need to watch for unusual API call patterns, weird data transfers, or someone trying to manipulate API parameters for access they shouldn't have. Let's talk about how to spot these red flags before they turn into full-blown security disasters.
The Tell-Tale Signs: Identifying Suspicious Behavior Patterns#
Let's get real about catching insider threats — it's all about spotting behavior that just doesn't look right. Once you know the patterns, you'd be surprised how obvious some warning signs can be.
Data Exfiltration Signals#
You know what most insider threats are after? Your data. Watch for anyone downloading, transferring, or accessing information they normally wouldn't touch. If your front-end developer suddenly starts making calls to your customer database API at 2 AM, you might want to ask some questions.
Privilege Abuse Patterns#
Some folks just can't resist trying to access things they shouldn't. Look for repeated attempts to hit restricted endpoints or clever parameter manipulation to bypass your security. It's like watching someone try every window in your house after finding the front door locked.
Location and Timing Anomalies#
Sometimes the red flags are just plain obvious. Like when someone's credentials are accessing your API from Russia at 3 AM, but that person works in your Seattle office and is definitely asleep. Unless they've mastered the art of being in two places at once, something's wrong.
Unintentional Threat Behaviors#
Not all threats come from bad intentions. Sometimes, it's just an honest mistake — someone accidentally accessing restricted resources or falling for a phishing attack that compromised their credentials. These folks aren't villains, but they can still cause damage if you don't catch the issue fast.
The key is knowing what's normal first. Is this person usually accessing these APIs? From this location? At this time? With this much data? When the answers start being "no," it's time to investigate. And this is where good monitoring tools earn their keep - they can spot these deviations and alert you before real damage happens.
Building Your Defense: Core Security Principles#
Enough theory — let's talk about the foundational elements and API security best practices you need to lock down your APIs against insider threats.
Additionally, ensuring adherence to security and compliance policies is essential in building a robust defense.
The Principle of Least Privilege#
The most fundamental security concept is giving users only what they absolutely need. Despite being security 101 for decades, it's still surprisingly underimplemented. When properly implemented, least privilege dramatically improves your security posture by:
- Reducing your overall attack surface — every API endpoint a user can't access is one less vulnerability
- Limiting lateral movement potential if credentials are compromised
- Preventing malware from gaining elevated privileges through compromised accounts
For API developers, implementing application-specific elevation of rights rather than granting blanket access allows necessary tasks without compromising security. Refer to our Basic Authentication guide for more information.
Additionally, securing your backend with shared secrets is a key part of backend API security.

Over 10,000 developers trust Zuplo to secure, document, and monetize their APIs
Learn MoreSeparate Privilege Levels#
Create clear separation between different access levels:
- Set default user privileges at a standard level for all personnel
- Create separate accounts for users who need elevated privileges—one for routine tasks like email, another for admin work
- Remove root and admin access to API endpoints where possible
- Assign users to specific admin groups with precisely tailored permissions (e.g., "API Configuration Admins")
Think of it like having separate keys for your house and your safe. You don't use the safe key every day, and you certainly don't leave it lying around.
Role-Based Access Control#
Instead of managing permissions individually, create roles that match job functions and assign users to those roles. This approach, known as RBAC for permission management:
- Simplifies permission management by grouping related access rights
- Reduces permission creep as employees change roles
- Makes auditing easier with clear visibility of who has what access
- Enables faster onboarding by simply assigning appropriate roles
For APIs, create distinct roles for different access types—read-only, write access, configuration access—giving you precise control over who can do what. Monitoring RBAC analytics metrics helps in understanding permission usage and can further streamline access control.
Assign users to specific admin groups with precisely tailored permissions (e.g., "API Configuration Admins"), and consider implementing authentication methods like mTLS authentication policy to enhance security.
Advanced Monitoring Strategies#
Even with tight access controls, you still need to watch what's happening. Trust but verify, as they say.
Real-Time Visibility#
Comprehensive visibility is your foundation for effective security:
- Log all significant API interactions with detailed context
- Capture request parameters, response codes, timestamps, and user identities
- Track performance metrics that might indicate security issues
- Implement threshold-based alerting for unusual patterns
Implement tools for API metrics monitoring to track performance metrics that might indicate security issues.
Integrate your monitoring at the API gateway level to ensure consistent visibility across all your endpoints. Considering a hosted API gateway can provide additional benefits in terms of scalability and ease of management.
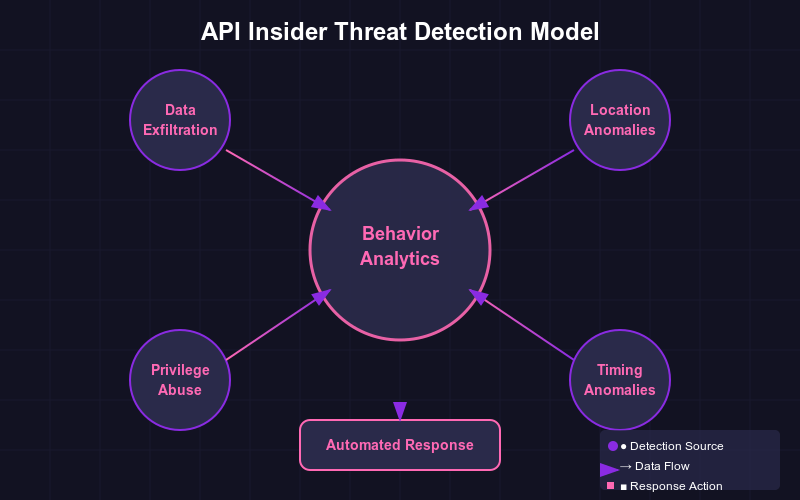
Behavior Analytics#
Basic monitoring tells you what's happening. Behavior analytics tells you if what's happening is normal:
- Create detailed profiles of typical usage patterns for users and services
- Apply machine learning to recognize normal patterns and flag deviations
- Consider contextual factors like role, location, and timing when evaluating behavior
- Continuously refine detection models to reduce false positives
These systems get smarter over time, gradually improving their ability to distinguish between legitimate changes in behavior and genuinely suspicious activities. For more on this topic, check out these API analytics best practices.
Automated Response Mechanisms#
The best security systems don't just detect threats — they respond to them:
- Temporarily suspend access when truly suspicious activities are detected
- Implement step-up authentication for unusual access patterns
- Alert security teams in real-time about high-risk behaviors
- Generate detailed forensic information to support investigations
This integration creates a closed-loop system that both identifies and mitigates potential threats before significant damage occurs.
Your API Protection Action Plan: From Detection to Response#
Now, let's create a practical action plan that takes you from identifying potential problems to implementing a comprehensive security system.
Map Your API Landscape#
You can't protect what you don't know exists. Start with a complete inventory of what you have.
- Discover all your APIs — including the "shadow APIs" teams might have created without going through official channels
- Document who has access to what (and who should have access)
- Identify your high-value targets — the APIs that access sensitive data or critical functionality
- Establish baseline usage patterns so you'll know when something looks off
Implement Advanced Monitoring#
Once you know what you're protecting, set up the right visibility tools.
- Deploy comprehensive API activity logging with enough detail to reconstruct incidents
- Set up real-time alerts for suspicious patterns — unusual access times, unexpected data volumes, repeated authentication failures
- Use behavior analytics to identify subtle anomalies that simple rule-based monitoring might miss
- Establish regular review cycles for security logs and alerts
Create Your Incident Response Playbook#
When you detect suspicious activity, you need a clear plan of action.
- Develop detailed response procedures for different types of security incidents
- Define clear escalation paths and decision-making authority
- Train your team on these procedures through regular drills and simulations
- Document everything for both post-incident analysis and compliance purposes
Build a Continuous Improvement Cycle#
Security is never "done" — it's an ongoing process of adaptation.
- Schedule regular security reviews as your organization and systems evolve
- Refine your detection tools based on both hits and false alarms
- Stay current on emerging threats and attack techniques
- Regularly test your security controls to ensure they're working as intended
Future Trends: The Evolving Landscape of API Security#
The world of API security never stands still. As technologies evolve and threat actors become more sophisticated, staying ahead of the curve requires awareness of emerging trends. Let's look at what's shaping the future of insider threat protection for APIs.
Zero Trust Architecture#
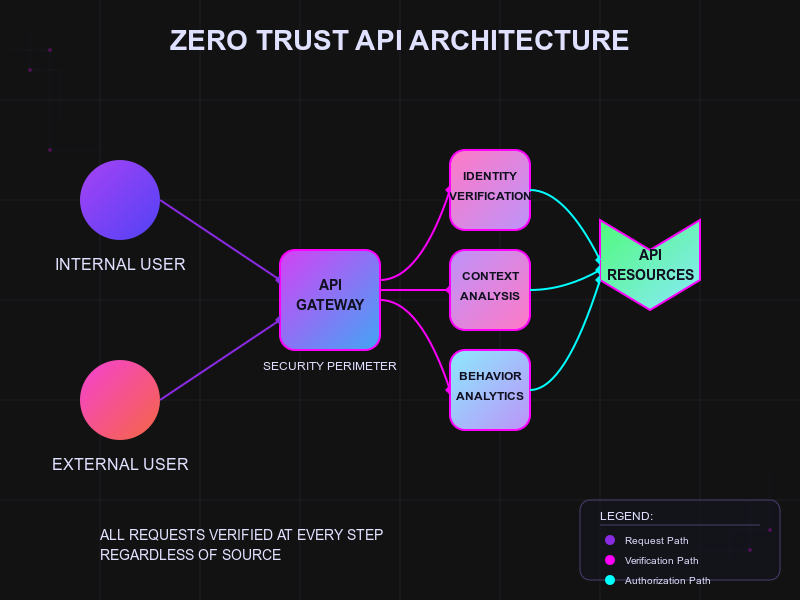
Traditional security models operate on the assumption that everything inside an organization's network can be trusted. Zero Trust flips this notion on its head with a simple principle: never trust, always verify.
This approach is particularly effective against insider threats because it treats every request as potentially malicious, regardless of where it originates. For APIs, this means:
- Continuous verification of every API call, even from internal sources
- Contextual authentication that considers not just credentials, but device health, location, time of day, and user behavior
- Micro-segmentation that limits lateral movement between systems
- Just-in-time access provisioning instead of standing privileges
As zero trust adoption grows, expect to see more granular API security controls that verify not just who is making a request, but whether that request matches expected patterns and behaviors.
AI-Powered Threat Detection#
The volume and complexity of API traffic have outgrown traditional rule-based security approaches. Machine learning and AI are stepping in to fill the gap with systems that can:
- Automatically establish baseline behaviors for users, applications, and services
- Detect subtle anomalies that would be invisible to conventional monitoring
- Predict potential security incidents before they occur
- Continuously improve by learning from both true and false positives
These capabilities are particularly valuable for insider threat detection, where the line between legitimate and suspicious behavior can be extremely thin. AI systems can spot patterns that might indicate credential compromise or data exfiltration attempts far earlier than human analysts could.
Unified API Governance#
As organizations push toward digital transformation, the number of APIs they manage continues to multiply. This sprawl has created governance challenges that future security approaches will need to address:
- Centralized API discovery and inventory management to eliminate shadow APIs
- Automated compliance monitoring across all API endpoints
- Consistent security policy enforcement regardless of where APIs are deployed
- Integrated security testing throughout the API lifecycle
The trend is moving toward unified governance platforms that provide visibility and control across the entire API ecosystem, making it harder for insiders to exploit gaps between different systems or teams.
Shift-Left Security#
Rather than treating security as something to add after development, organizations are increasingly "shifting left" by integrating security into the earliest stages of API development:
- Security-as-code approaches that build access controls directly into API specifications
- Automated security testing as part of CI/CD pipelines
- Developer-friendly security tools that catch potential vulnerabilities during coding
- Threat modeling exercises before new APIs are designed
This trend promises to reduce the attack surface available to potential insider threats by eliminating common vulnerabilities before APIs even reach production.
The Path Forward: Securing Your APIs from the Inside Out#
Protecting your APIs from insider threats isn't just a technical challenge—it's a business imperative. With the right combination of access controls, monitoring capabilities, and response procedures, you can significantly reduce the risk of data breaches, service disruptions, and other security incidents that could impact your organization's reputation and bottom line.
Ready to strengthen your API security posture? Zuplo offers powerful tools for implementing robust access controls, monitoring API usage, and detecting suspicious activities across your API ecosystem. Sign up for a free Zuplo account today and take the first step toward comprehensive protection against insider threats.









