Implementing Content Security Policy for API Protection: A Comprehensive Guide
Major companies fall victim to cross-site scripting attacks with alarming frequency, and the consequences can be devastating. Content Security Policy (CSP) gives you powerful control over which resources can be loaded and executed by your web applications and APIs, creating a crucial line of defense against these persistent threats.
For APIs specifically, CSP is a game-changer. It controls which external resources your API can interact with, limits unauthorized data access, and manages third-party script execution. These capabilities don't just provide theoretical security benefits—they give you practical, granular control that works alongside your existing server-side protections.
Let's dive into how you can harness CSP to protect your APIs from today's most common and dangerous threats.
- Demystifying Content Security Policy: What You Need to Know
- API-Specific CSP Implementation: Different from Traditional Web Apps
- Essential CSP Directives for Bulletproof API Security
- Advanced Techniques: Nonce-based and Hash-based CSP
- Testing and Monitoring: Ensuring Ongoing Protection
- CSP Best Practices: Your API Security Checklist
- Taking Your API Security to the Next Level
Demystifying Content Security Policy: What You Need to Know#
The security landscape never stops evolving, and attackers keep finding creative new ways to exploit vulnerabilities. Content Security Policy has become an essential tool in the modern developer's security arsenal. But what exactly is it, and how does it protect your APIs?
The Mechanics Behind CSP#
CSP operates through a set of directives specified in HTTP headers or HTML meta tags. When a browser loads your page or interacts with your API, it checks these directives against any content being loaded and automatically blocks anything that doesn't comply with your rules.
The syntax is refreshingly straightforward:
Content-Security-Policy: <policy-directive>; <policy-directive>
Each directive sets boundaries around which types of resources can be loaded and from where. For example, script-src 'self' only allows scripts from your own domain to run. This simple rule immediately blocks potentially malicious scripts from other sources without requiring you to identify each threat individually.
Why CSP Matters for Your API Security#
For APIs, CSP works like a sophisticated filtering system. It blocks unauthorized scripts, dramatically reducing XSS risks that could compromise your entire system. It controls data transmission paths, shutting down data exfiltration attempts before sensitive information leaves your environment.
CSP also restricts resource loading to trusted sources, shrinking your attack surface and making it harder for attackers to find ways in. This protection covers everything connected to your API – documentation pages, management consoles, and web interfaces.
Well-implemented CSP policies block most XSS attack vectors while also giving you insights into attempted breaches. These insights help you continuously improve your security posture by revealing real-world attack patterns against your specific implementation.
Common Vulnerabilities That CSP Addresses#
A properly implemented CSP protects against cross-site scripting by controlling which scripts can run in the context of your application. It prevents clickjacking attempts by defining which sites can frame your content, ensuring your users don't unknowingly interact with disguised interfaces.
CSP also mitigates data injection attacks by restricting what resources can be loaded, preventing attackers from inserting malicious code. It blocks malware infections by preventing loading from malicious domains, keeping your API environment clean from persistent threats.
Each of these protections works together to create layers of security that are difficult for attackers to penetrate. By addressing these common vulnerabilities, CSP significantly reduces your overall security risk with minimal performance impact.
API-Specific CSP Implementation: Different from Traditional Web Apps#
Trying to apply traditional web app CSP techniques to APIs is like using submarine blueprints to build an airplane. Both operate in completely different environments, and understanding these differences is crucial for your security strategy.
Architectural Differences That Matter#
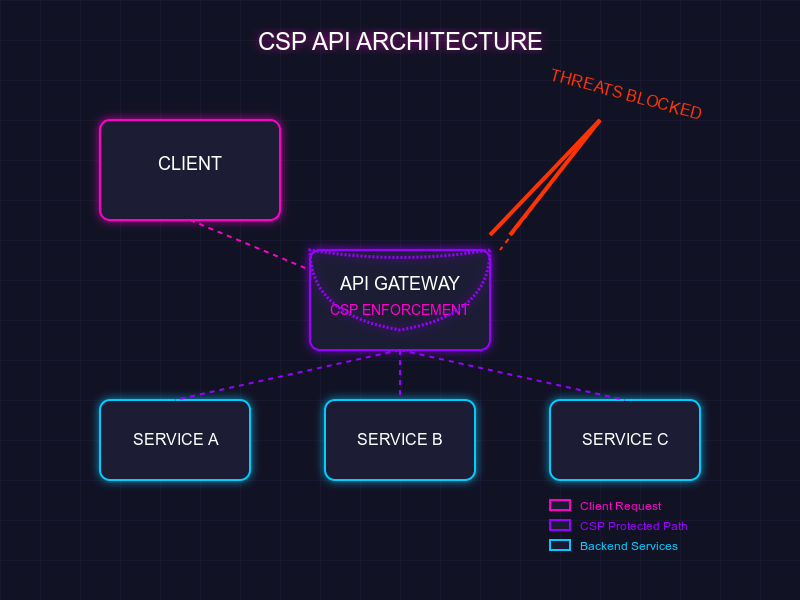
Traditional web applications serve complete HTML pages with embedded resources, while APIs primarily deliver data in formats like JSON without presentation elements.
This fundamental difference completely transforms your security approach. Web apps require protection for numerous resource types, making CSP implementation complex with multiple directives. For APIs, many traditional CSP directives become almost irrelevant. Your focus shifts to data integrity, unauthorized access prevention, and rate limiting instead.
Unique Challenges in API Environments#
When securing APIs with CSP, you'll encounter several specific challenges. Many CSP directives were designed for HTML contexts, making them awkward fits for pure API responses. This HTML disconnect requires you to be selective about which directives you implement.
APIs often need to serve multiple clients across different origins, requiring careful balance between security and accessibility. This CORS complexity introduces additional considerations for your CSP strategy, as overly restrictive policies might break legitimate functionality.
Multiple API endpoints with varying security requirements make consistent CSP implementation challenging. What works for one endpoint might be too restrictive or too permissive for another, requiring thoughtful policy design.
APIs routinely connect with external services, necessitating dynamic CSP policies. These third-party integrations introduce potential vulnerabilities that must be managed carefully without disrupting business operations.
Best Practices for API-Focused CSP#
To implement CSP effectively in API environments, lock down your Content-Types (like Content-Type: application/json) to prevent content sniffing attacks. This simple step prevents browsers from interpreting your API responses as executable content.
Focus on API-relevant directives such as connect-src, frame-ancestors, and form-action instead of trying to implement every available directive. This targeted approach provides better security with less complexity.
Start with Report-Only mode to identify potential issues before enforcing restrictions. This allows you to collect data on what would be blocked without disrupting your users, giving you confidence before enforcement.
Implement CSP at the API gateway level for consistent protection across all endpoints. This central implementation ensures that all API traffic is protected regardless of which backend services are involved.
Essential CSP Directives for Bulletproof API Security#
When it comes to protecting your APIs with CSP, certain directives do the heavy lifting while others barely register on the security Richter scale. Let's focus on the ones that truly matter for API security.
The Foundation: default-src#
The default-src directive serves as your security baseline – the fallback rule that applies when you haven't specified something more targeted:
Content-Security-Policy: default-src 'self';
By setting default-src to 'self', you restrict all resource loading to your own domain by default. This single directive creates a strong security foundation without complex configurations, protecting against many common attack vectors.
Critical for APIs: connect-src#
The connect-src directive is the crown jewel of API security as it controls which URLs your API can connect to:
Content-Security-Policy: connect-src 'self' https://api.example.com;
This directive limits API connections to only your specified trusted sources. It's particularly effective for preventing data exfiltration, where attackers attempt to send sensitive data to external servers. With proper connect-src settings, those attempts are automatically blocked.
Protecting Interactive Elements: script-src#
For APIs with browser-rendered components (like documentation or admin panels), the script-src directive provides essential protection:
Content-Security-Policy: script-src 'self' 'nonce-{RANDOM}' 'strict-dynamic';
This directive limits which JavaScript can execute, dramatically reducing XSS risk. Adding nonces (one-time codes) and strict-dynamic enhances your protection, ensuring only approved scripts run – even in complex applications.
### **Clickjacking Prevention: frame-ancestors**
The `frame-ancestors` directive specifies which sites can embed your content:
Content-Security-Policy: frame-ancestors 'none';
Setting this to `'none'` prevents your API interface, management console, or documentation from being framed by other sites. This protection stops clickjacking attacks where users might unknowingly interact with disguised malicious interfaces.
### **Ensuring Encrypted Connections: upgrade-insecure-requests**
For comprehensive transport security:
Content-Security-Policy: upgrade-insecure-requests;
This directive automatically upgrades HTTP requests to HTTPS, preventing accidental insecure connections and man-in-the-middle attacks. It's particularly useful during migrations or when dealing with legacy systems that might still contain HTTP references.
### **Monitoring Security: report-uri / report-to**
For visibility into potential security issues:
Content-Security-Policy: report-uri https://example.com/csp-reports;
These directives tell browsers where to send reports when something violates your policies. They provide valuable insights into potential attacks and misconfiguration issues before they become serious problems.
## **Practical Implementation Guide: Language Specific Approaches**

Ready to [implement CSP](https://developer.mozilla.org/en-US/docs/Web/HTTP/CSP) in your API? Here's how to do it across different programming languages and frameworks, with practical code examples that you can adapt to your environment.
### **Node.js (Express) Implementation**
Express makes it easy to implement CSP through middleware:
```javascript
const express \= require('express');
const app \= express();
// Define CSP middleware
const cspMiddleware \= (req, res, next) \=\> {
res.setHeader(
'Content-Security-Policy',
"default-src 'self'; script-src 'self' 'nonce-{RANDOM\_NONCE}'; object-src 'none'"
);
next();
};
// Apply CSP middleware to all routes
app.use(cspMiddleware);
// Example API route
app.get('/api/data', (req, res) \=\> {
res.json({ message: 'API response' });
});
app.listen(3000, () \=\> console.log('API running on port 3000'));
This middleware sets a CSP header on all responses, restricting resources to the same origin and using nonces for script execution.

Over 10,000 developers trust Zuplo to secure, document, and monetize their APIs
Learn MorePython (Flask) Implementation#
In Flask, you can use the Flask-Talisman extension:
from flask import Flask, jsonify
from flask\_talisman import Talisman
app \= Flask(\_\_name\_\_)
csp \= {
'default-src': "'self'",
'script-src': "'self' 'nonce-{nonce}'",
'object-src': "'none'"
}
Talisman(app, content\_security\_policy=csp)
@app.route('/api/data')
def get\_data():
return jsonify({'message': 'API response'})
if \_\_name\_\_ \== '\_\_main\_\_':
app.run(port=3000)
Flask-Talisman not only adds CSP headers but also handles other security headers automatically.
Java (Spring Boot) Implementation#
For Spring Boot applications, configure CSP in your security configuration:
import org.springframework.context.annotation.Configuration;
import org.springframework.security.config.annotation.web.builders.HttpSecurity;
import org.springframework.security.config.annotation.web.configuration.EnableWebSecurity;
import org.springframework.security.config.annotation.web.configuration.WebSecurityConfigurerAdapter;
@Configuration
@EnableWebSecurity
public class SecurityConfig extends WebSecurityConfigurerAdapter {
@Override
protected void configure(HttpSecurity http) throws Exception {
http
.headers()
.contentSecurityPolicy("default-src 'self'; script-src 'self' 'nonce-{nonce}'; object-src 'none'");
}
}
Spring Security provides built-in support for adding security headers, including CSP.
Framework-Specific Considerations#
Different API frameworks require different approaches:
- RESTful APIs: Implement CSP as middleware or filter and apply headers consistently
- GraphQL APIs: Apply CSP headers to GraphQL endpoint responses and be careful with inline scripts in GraphQL playgrounds
- Serverless APIs: Ensure CSP headers are included in function responses consistently
Advanced Techniques: Nonce-based and Hash-based CSP#
While basic CSP implementations provide solid protection, advanced strategies like nonce-based and hash-based approaches can significantly enhance your security posture.
Nonce-based CSP: Dynamic Protection#
Nonce-based CSP uses a randomly generated value to authorize specific scripts for execution. The server generates a unique nonce for each page load, providing enhanced security against script injection.
Implementation steps:
- Generate a cryptographically strong random nonce for each HTTP response
- Include the nonce in your CSP header
- Add the nonce attribute to all script tags
Here's an example using Express.js:
const crypto \= require('crypto');
app.use((req, res, next) \=\> {
const nonce \= crypto.randomBytes(16).toString('base64');
res.locals.nonce \= nonce;
res.setHeader('Content-Security-Policy',
\`script-src 'nonce-${nonce}' 'strict-dynamic'; object-src 'none'; base-uri 'none';\`);
next();
});
Nonce-based CSP works exceptionally well with server-side rendered pages but can be challenging to implement with static hosting or heavy caching.
Hash-based CSP: Perfect for Static Content#
Hash-based CSP uses cryptographic hashes of allowed scripts to determine execution permissions. This approach is particularly effective for static content and single-page applications.
Implementation steps:
- Calculate the hash of each inline script
- Include the hashes in your CSP header
Here's how to generate a hash for an inline script:
echo \-n 'console.log("Hello, CSP\!");' | openssl dgst \-sha256 \-binary | openssl base64 \-A
The resulting hash would be included in your CSP header like this:
Content-Security-Policy: script-src 'sha256-{HASHED\_INLINE\_SCRIPT}' 'strict-dynamic'; object-src 'none'; base-uri 'none';
Hash-based CSP works well with static content but requires recalculation whenever scripts change.
Integration Strategy for API Architecture#
When integrating advanced CSP into API architectures:
- Implement CSP headers at the API gateway level for consistent policy application
- Use nonce-based CSP for services generating dynamic HTML
- Apply hash-based CSP for services serving static assets
- Set up a central reporting endpoint for CSP violations
Testing and Monitoring: Ensuring Ongoing Protection#
Implementing CSP is just the beginning. Continuous testing and monitoring are essential for maintaining effective protection over time.
Report-Only Mode: Testing Without Breaking Things#
Before fully enforcing your CSP policies, use the Content-Security-Policy-Report-Only header:
Content-Security-Policy-Report-Only: default-src 'self'; report-uri /csp-violation-report
This allows you to monitor policy violations without affecting functionality. Violation reports are sent as JSON data to your specified endpoint:
{
"csp-report": {
"document-uri": "...",
"referrer": "...",
"violated-directive": "...",
"effective-directive": "...",
"original-policy": "...",
"blocked-uri": "...",
"status-code": 200
}
}
Start with permissive policies and gradually tighten restrictions as you analyze these reports.
Setting Up Effective Violation Reporting#
To get started with CSP violation reporting:
- Configure the Reporting-Endpoints header:
Reporting-Endpoints: csp-endpoint="[https://example.com/csp-reports](https://example.com/csp-reports)"- Include the report-to directive in your CSP header:
Content-Security-Policy: default-src 'self'; report-to csp-endpoint- Implement an endpoint to receive and process these reports:
app.post('/csp-report-endpoint', (req, res) \=\> {
console.log('CSP Violation:', req.body);
res.status(204).end();
});
- For maximum browser compatibility, use both report-uri and report-to directives.
Continuous Monitoring Tools#
Several platforms can help you monitor CSP effectiveness. For instance:
- Datadog offers specialized CSP monitoring with automatic trend detection
- Sentry provides detailed violation reports with context
- Custom logging solutions can be integrated with your existing monitoring stack
Regular monitoring of these reports is crucial for maintaining an effective security posture while balancing functionality.
CSP Best Practices: Your API Security Checklist#
Security experts have developed effective approaches to CSP implementation through years of practical experience. These proven strategies can strengthen your API security without having to learn everything the hard way.
Start with a Solid Foundation#
A strong foundation for your CSP implementation ensures you get maximum security benefits from the beginning. These core practices help you establish effective protection while minimizing disruption:
- Implement the principle of least privilege. Only allow the resources that are absolutely necessary for your API to function, creating a minimal attack surface that's significantly harder for attackers to exploit.
- Begin with CSP in Report-Only mode before enforcing. This allows you to gather data on what would be blocked without disrupting your users, giving you confidence before switching to enforcement mode.
- Centralize your CSP headers in a configuration management system. A central repository ensures consistency and makes updates more efficient across your entire API ecosystem.
- Develop separate policies for different environments. Your development environment needs more flexibility, while production requires the strictest controls to properly balance security with the practical needs of each context.
Optimize for Long-term Maintenance#
CSP isn't a set-it-and-forget-it solution. These maintenance practices will help ensure your CSP implementation remains effective as your API evolves over time:
- Document your CSP strategy and the reasoning behind specific directives. Comprehensive documentation helps future developers understand your security decisions and prevents inadvertent weakening of your security posture during modifications.
- Include CSP validation in your CI/CD pipeline with automated testing. These tests can verify that code changes don't introduce new CSP violations, preventing gradual security degradation as your application evolves.
- Establish a formal review process for CSP modifications. Having multiple team members evaluate security-critical changes significantly reduces the risk of mistakes that could open security holes.
- Create a dedicated channel for collecting and reviewing violation reports. These reports reveal attempted attacks and highlight configuration issues, allowing you to continuously refine your security posture based on real-world data.
Balance Security and Functionality#
Finding the right balance between strict security and necessary functionality is a key challenge with CSP. These practices help you maximize protection without breaking legitimate features:
- Use nonces instead of 'unsafe-inline' whenever inline scripts are necessary. This approach allows you to permit required inline scripts while maintaining strong security by requiring a unique token that attackers can't predict.
- Implement hash-based CSP validation for static resources that rarely change. By specifying cryptographic hashes of approved resources in your policy, you can validate content without the complexity of managing nonces.
- Advocate for third-party vendors to support modern CSP practices. Rather than weakening your security to accommodate outdated services, push external providers to support security features like nonce-based CSP.
- Combine CSP with other security measures as part of a defense-in-depth approach. Layer CSP with HTTPS, authentication, input validation, and output encoding to create multiple barriers that attackers must overcome.
Look To the Future#
The security landscape continues to evolve rapidly. These forward-looking practices help you stay ahead of emerging threats and leverage new protection capabilities:
- Explore how CSP works with newer protections like Trusted Types. This emerging standard specifically targets DOM-based XSS attacks, adding another layer of protection that complements your CSP implementation.
- Monitor the transition from
report-urito the newerReporting-Endpointsheader. Staying current with evolving specifications ensures your implementation remains compatible with browser changes. - Evaluate how emerging standards like Cross-Origin Isolation integrate with your CSP strategy. These new security features can provide even stronger protection against sophisticated attacks while maintaining compatibility.
- Schedule regular reviews of CSP specifications and browser implementations. Following security blogs, standards documentation, and browser release notes will help you maintain effective protection as the threat landscape evolves.
Taking Your API Security to the Next Level#
Content Security Policy isn't just another box to check on your security to-do list—it's a powerful tool that gives you precise control over what resources can interact with your API. When implemented strategically, CSP dramatically reduces your vulnerability to XSS, injection attacks, and data theft.
Ready to give your APIs the protection they deserve? Zuplo's API management platform makes implementing robust CSP policies surprisingly simple. With centralized policy management, built-in testing tools, and real-time monitoring, you can secure your APIs without becoming a security expert. Sign up for a free Zuplo account and see how modern API security can elevate your protection.








